Apple Vision Pro wearers now have a new spatial note-taking app to try, and it's from one of Apple's arch rivals
Microsoft has announced an Apple Vision Pro OneNote app and it's available for download now.

iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
By Oliver Haslam published
Adobe has previewed new generative AI features coming to Premiere Pro designed to make creating video and audio easier.

By Oliver Haslam published
Spotify's lossless music offering might finally be on the way as part of the Music Pro add-on.

By Connor Jewiss published
More iPhone 16 dummy units have leaked sporting the same design as before, seemingly confirming the device's new design.

By John-Anthony Disotto published
Quick Tips Turn off the annoying in-app review request pop-ups on your iPhone and get back to the tasks that matter.

By Connor Jewiss published
More iPhone 16 dummy units have leaked sporting the same design as before, seemingly confirming the device's new design.

By Connor Jewiss published
There's a new iPhone case from Bitmo Lab that comes with its own motherboard and power supply to give you another shorcuts button you can customize

By Oliver Haslam published
Rode has announced two new accessories designed to give creators more flexibility while remaining mobile.

By Stephen Warwick published
A new report says Apple's OLED iPad could drive a 600% increase in OLED tablet sales in 2024.

By Tammy Rogers published
The iPad Air 5 is currently at its lowest price ever, although we don't think you should buy one right now — wait until the new ones come out instead.

By Joe Wituschek published
Opinion If there's one thing I want from the next-generation iPad mini, it's that long-rumored OLED display.

By Oliver Haslam last updated
The next iPad Pro refresh is set to bring new chips and fancier displays in 2024.

By John-Anthony Disotto last updated
Transfer photos, music, and watch movies with our pick of the best CD and DVD drives for Mac.

By Gerald Lynch published
The Satechi Thunderbolt 4 Slim Pro Hub is excellent — if all you need is more Thunderbolt ports for your Mac and practically nothing else.

By Daryl Baxter published
Opinion It’s mainly agreed that Apple’s solution to replace the function row was a failure — what if it came back as an app?
By Lloyd Coombes published
Apple's new chip could make its debut this year, according to Mark Gurman.

By John-Anthony Disotto published
Quick Tips There's a temporary fix for ghost touch on Apple Watch but you'll need to wait for a more permanent one.

By James Bentley published
What are the best accessories for Apple Watch? From high-tech chargers to cool carry bags, we have a few ideas!

By John-Anthony Disotto published
Quick Tips This Apple Watch trick will make charging your smartwatch that much easier and it's been under our noses the whole time.
By Alex Blake published
Noir adds a dark mode to every website, making each one easier to read and better for your eyesight.

By John-Anthony Disotto published
Quick Tips Turn off the annoying in-app review request pop-ups on your iPhone and get back to the tasks that matter.
By John-Anthony Disotto last updated
Is your iPhone not receiving pictures? Luckily there are a couple of things to try to fix this annoying issue.
By Stephen Warwick last updated
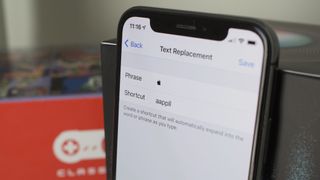
Here's how to quickly type the Apple logo emoji on iPhone and iPad. Find the Apple symbol with ease.

By John-Anthony Disotto published
Quick Tips You probably aren't taking iPhone photos in 48MP but you should with this simple HEIF Max setting that adds more detail to your pictures.

By James Bentley published
Civilization VI has been unable to launch for over a month now on iPad and iPhone and we don’t quite know why.

By James Bentley published
With a new update on the way for Sonic Dream Team, we had the chance to chat with Sega Hardlight, its developer to find out more.

By James Bentley published
If you own an iPhone, it may be about to become a much better device for gaming.

By Gerald Lynch published
The Satechi Thunderbolt 4 Slim Pro Hub is excellent — if all you need is more Thunderbolt ports for your Mac and practically nothing else.

By John-Anthony Disotto published
The BenQ beCreatus DP1310 is the perfect dock for Mac users who play games on console. With just one click you can jump between USB-C and HDMI 2.1.
By Alex Blake published
Stage View adds previews to apps and windows in the Stage Manager sidebar. Is it worth your cash?

By Tammy Rogers published
The Geekom A7 is a powerful, tiny, and very well-priced mini PC — but should you choose one over the Mac mini?

By Alex Blake published
The Logitech Signature Slim K950 is a more affordable version of the MX Keys S, with a similar typing feel but without a few nice-to-haves.

By Oliver Haslam published
Adobe has previewed new generative AI features coming to Premiere Pro designed to make creating video and audio easier.

By Oliver Haslam published
Spotify's lossless music offering might finally be on the way as part of the Music Pro add-on.

By Becca Caddy published
App of the day Sky Guide has long been my top choice for stargazing, but Night Sky is a close second.

By Olivia Powell last updated
Keep your Mac devices secure, and shore up your digital privacy, with our expert-recommended VPNs. Here are the best options on the market today.