
macOS 15 set to get a revamped and smarter Calculator app that looks like the one on iOS
According to a new report, the upcoming macOS 15 update is set to include a revamped and smarter Calculator app that looks like the one on iOS.

iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
By Becca Caddy published
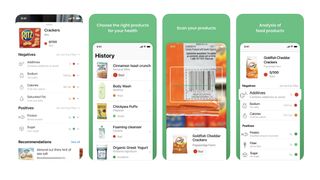
App of the day Yuka gives you more info about your groceries and flags healthy choices, ideal if you can't decide what to buy.

By Oliver Haslam published
Buying an Apple Watch Ultra 2 just got cheaper in China after Apple started rolling out refurbished models in the country.

By Oliver Haslam last updated
It's inevitable that the iPad Air lineup will get a refreshed model and here's what we've been hearing so far.
By Daryl Baxter published
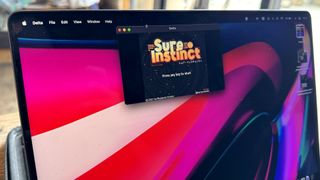
Delta has been found to work on Apple Vision Pro, as well as a Mac, but you’ll have a hard time using it without a controller.

By Stephen Warwick published
Apple's iPhone 16 is fast approaching, but what about Apple's future plans for iPhone next year?

By John-Anthony Disotto published
Quick Tips Your iPhone has a hidden sound library with calming noises like white noise and rain.

By Connor Jewiss published
According to a new report, the iPhone 17 may offer a new display size that sits between the regular and Pro models.

By Oliver Haslam last updated
It's inevitable that the iPad Air lineup will get a refreshed model and here's what we've been hearing so far.

By James Bentley published
The iPad Air 6 is tipped to receive new upgrade, giving it a much nicer screen.
By Stephen Warwick last updated
Each iPad lineup offers different storage configurations, so let's run through all of them for you.

By Stephen Warwick published
Apple's OLED iPad Pro is close at hand, but several well-established Android rivals already have devices on the market.
By Stephen Warwick last updated
With the advent of Apple silicon, gaming on Mac is better than ever. But what's the best gaming MacBook you can buy right now?

By Stephen Warwick published
2024 could herald the first wave of M4 Macs, what do we know about the next generation of Apple silicon?

By Stephen Warwick published
Qualcomm says its Snapdragon X Elite bests Apple's M3 Mac in some benchmark tests, but other results are missing...

By John-Anthony Disotto last updated
Transfer photos, music, and watch movies with our pick of the best CD and DVD drives for Mac.

By Oliver Haslam published
Buying an Apple Watch Ultra 2 just got cheaper in China after Apple started rolling out refurbished models in the country.

By John-Anthony Disotto published
Quick Tips There's a temporary fix for ghost touch on Apple Watch but you'll need to wait for a more permanent one.

By James Bentley published
What are the best accessories for Apple Watch? From high-tech chargers to cool carry bags, we have a few ideas!

By John-Anthony Disotto published
Quick Tips This Apple Watch trick will make charging your smartwatch that much easier and it's been under our noses the whole time.

By Stephen Warwick last updated
iOS 17 has lots of tools to block certain types of websites, specific URLs, or any website except ones you've allowed.

By Matt Evans published
Connecting your Apple Watch to treadmills, exercise bikes and other fitness equipment brings outdoor accuracy inside.

By John-Anthony Disotto published
Quick Tips Your iPhone has a hidden sound library with calming noises like white noise and rain.

By John-Anthony Disotto last updated
How-to How to transfer data from iPhone to iPhone, so your shiny new device works straight out of the box.

By James Bentley published
PPSSPP, a PSP emulator for iPhone, is currently in the works but Apple’s unclearness around its own rules leaves the developer unsure of if it will launch.

By James Bentley last updated
Fortnite isn't on The App Store, but you can still play it on iPhone or iPad for free. Here's how to play Fortnite on iPhone or iPad in just a few simple steps.

By James Bentley published
A Virtual Boy Emulator is coming to Apple Vision Pro, letting users play a piece of VR history

By James Bentley published
The Lofree Dot Foundation is a gorgeous mechanical keyboard that takes its looks from makeup. Our review:

By Gerald Lynch published
The Satechi Thunderbolt 4 Slim Pro Hub is excellent — if all you need is more Thunderbolt ports for your Mac and practically nothing else.

By John-Anthony Disotto published
The BenQ beCreatus DP1310 is the perfect dock for Mac users who play games on console. With just one click you can jump between USB-C and HDMI 2.1.
By Alex Blake published
Stage View adds previews to apps and windows in the Stage Manager sidebar. Is it worth your cash?

By Tammy Rogers published
The Geekom A7 is a powerful, tiny, and very well-priced mini PC — but should you choose one over the Mac mini?

By Alex Blake published
The Logitech Signature Slim K950 is a more affordable version of the MX Keys S, with a similar typing feel but without a few nice-to-haves.

By Becca Caddy published
App of the day Yuka gives you more info about your groceries and flags healthy choices, ideal if you can't decide what to buy.

By Oliver Haslam published
Roadtrip is a new app to the UK where it now promises to offer customized data on which routes and fuel stops to use to save money on journeys.
By Becca Caddy published
App of the day If you're looking for an alternative to Duolingo, Busuu might not be as fun and colorful, but it's simple and effective.

By Oliver Haslam published
WhatsApp has announced a new update to the way it lists chat threads with a new filter option.