Security
Latest about Security

Recent Apple iPhone spyware alerts could have been triggered by China-linked attacks, researchers say
By Oliver Haslam published
Recent alerts sent to iPhone users in 92 countries may have been linked to a spyware attack linked to China.
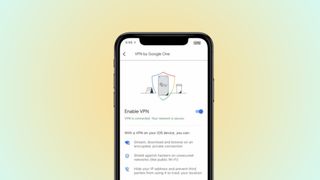
Google is about to give iPhone owners a privacy and security headache as it prepares to shut down another key service
By Oliver Haslam published
The Google One VPN is going away because, the company says, nobody ever used it.
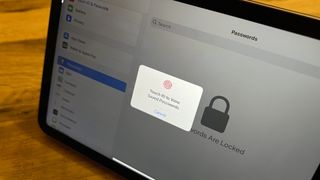
I can finally use iCloud Keychain and ditch 1Password thanks to this key new feature
By Oliver Haslam published
With the addition of shared password groups, iCloud Keychain is finally a viable alternative to 1Password and similar apps and services.

Old-school Mac malware is hiding in plain sight in this productivity app
By Oliver Haslam published
Old Mac malware has reappeared and it's pretending to be Microsoft software.

Researcher claims a key Mac security feature can be bypassed and Apple won't fix it
By Oliver Haslam published
A security researcher says that it made Apple aware of a Mac security flaw that is "trivially" easy to bypass but hasn't been fixed.
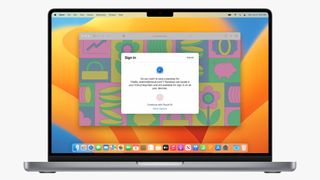
The apple.com website adds passkey support, but there's a catch
By Oliver Haslam published
The apple.com website now supports passkeys, but you'll need to be running Apple's latest betas to use them.

How can you keep your Apple devices and data safe? We asked the experts
By Alex Blake published
Stop data breaches and viruses in their tracks on your Mac, iPhone and iPad.

Passkeys just show how much Apple needs a real iCloud Keychain app
By Oliver Haslam published
There's still no iCloud Keychain app and it's beyond time there was.

1Password wants you to ditch passwords. The replacement could change everything
By Alex Blake published
Interview The security company explains why 2023 could be the year passkeys go stratospheric — and 1Password will be there to guide them.

Apple's secret Safari cookie crackdown could have unintended consequences for your logins
By Oliver Haslam published
Safari 16.4 treats cookies differently in an attempt to improve privacy, but it could also mean logging back into websites more often.
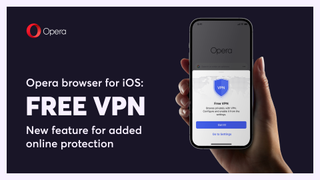
This free VPN is now available to all iPhone owners
By Oliver Haslam published
Opera is rolling out its free VPN service to everyone who uses its web browser on iPhone and iPad.

Urgent security updates for decade-old Macs and 8-year-old iPhones? So much for so-called 'planned obsolescence'
By Oliver Haslam published
Apple released iOS 15.7.5, iPadOS 15.7.5, macOS Big Sur 11.7.6, and Monterey 12.6.5 bringing important security fixes to older iPhones, iPads, and Macs.

1Password will keep all your passkeys safe in 2023
By Oliver Haslam published
1Password has announced that it will add support for passkeys starting in 2023 and it's joined the FIDO Alliance board, to boot.
You won't believe what the 88th most popular (and stupid) password of 2022 is
By Oliver Haslam published
A password management company has shared a list of the top 200 most common passwords of the year and it's a worrying read.

Apple settles trade secret theft lawsuit with former employee
By Palash Volvoikar published
Apple has settled its lawsuit against former materials lead Simon Lancaster, filed back in March 2021, accusing Lancaster of having sold company secrets to the media.

Your iPhone VPN isn't working as it should and Apple hasn't fixed it, says researcher
By Christine Chan published
While VPNs are a great way to hide and encrypt your data connection, you should be wary of using a VPN app on your iPhone or iPad right now.

You would be Wyze not to skip these incredible smart home security deals
By Nicholas Sutrich published
Feel wise this Black Friday with these incredible Wyze smart home security deals. Save up to 40% on some of the most affordable cameras, video doorbells, and security systems ever!

Apple files lawsuit against NSO Group stating it targets Apple users
By Luke Filipowicz published
Master your iPhone in minutes
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!


