Vice used the BlackVue dashcam app to track user location data in real time
What you need to know
- Vice tech outlet Motherboard was able to pull GPS location data for BlackVue users.
- It reverse-engineered the iOS app and tracked users over a week-long period.
- BlackVue has confirmed that this wasn't supposed to be possible and appears to have fixed the problem.
A report has revealed that GPS location data from the dashcam app BlackVue was available to be viewed and stored in real-time over days or even weeks, highlighting a significant security flaw in the app.
As revealed by Motherboard, Vice's tech branch, the report states:
BlackVue has an app that shows the location of drivers that opt-in. The creators say it shouldn't be possible to track its users in bulk; we found otherwise...BlackVue is a dashcam company with its own social network. With a small, internet-connected dashcam installed inside their vehicle, BlackVue users can receive alerts when their camera detects an unusual event such as someone colliding with their parked car. Customers can also allow others to tune into their camera's feed, letting others "vicariously experience the excitement and pleasure of driving all over the world," a message displayed inside the app reads.
The report then states:
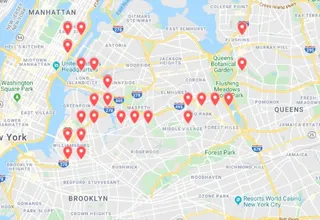
But what BlackVue's app doesn't make clear is that it is possible to pull and store users' GPS locations in real-time over days or even weeks. Motherboard was able to track the movements of some of BlackVue's customers in the United States.
BlackVue lets anyone create an account on its website for the purpose of viewing live broadcasts. Live broadcasting isn't on by default, it's an opt-in feature. According to BlackVue, a "tiny fraction" of BlackVue's overall customer base uses the feature. Broadcasting users are displayed on a map and you can tune into the feed in real-time. The available feeds are displayed on a map for selection, which is where it starts to get interesting. According to Motherboard:
But the actual GPS data that drives the map is available and publicly accessible... By reverse-engineering the iOS version of the BlackVue app, Motherboard was able to write scripts that pull the GPS location of BlackVue users over a week-long period and store the coordinates and other information like the user's unique identifier. One script could collect the location data of every BlackVue user who had mapping enabled on the eastern half of the United States every two minutes. Motherboard collected data on dozens of customers.
A BlackVue spokesperson said that "collecting GPS coordinates of multiple users over an extended period of time is not supposed to be possible", and speaking to Motherboard said:
"Our developers have updated the security measures following your report from yesterday that I forwarded."
Motherboard notes that several web requests that had previously provided user data were no longer functional. Thankfully, the issue has been highlighted and fixed. But up until now, it looks like BlackVue customers who had chosen to broadcast their feeds might well have got more than they bargained for.
Master your iPhone in minutes
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!

Stephen Warwick has written about Apple for five years at iMore and previously elsewhere. He covers all of iMore's latest breaking news regarding all of Apple's products and services, both hardware and software. Stephen has interviewed industry experts in a range of fields including finance, litigation, security, and more. He also specializes in curating and reviewing audio hardware and has experience beyond journalism in sound engineering, production, and design.
Before becoming a writer Stephen studied Ancient History at University and also worked at Apple for more than two years. Stephen is also a host on the iMore show, a weekly podcast recorded live that discusses the latest in breaking Apple news, as well as featuring fun trivia about all things Apple. Follow him on Twitter @stephenwarwick9
Most Popular



