Nick Arnott
Latest articles by Nick Arnott
Briefs 2 review: Quickly and easily prototype iOS and Android apps on your Mac
By Nick Arnott last updated

The Future of iPhone Security
By Nick Arnott last updated
The next major version of iOS could contain the most public and controversial security enhancements yet.

How Apple's Enterprise Distribution Program was abused to enable the installation of a GameBoy emulator
By Nick Arnott last updated

Why is the CurrentC app collecting your device information?
By Nick Arnott last updated

Coin wants to combine all of your cards into one, but how well will it work?
By Nick Arnott last updated
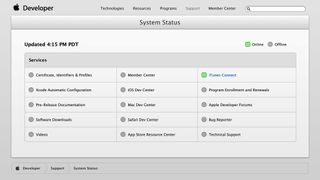
Apple discloses bug that was likely responsible for developer center downtime
By Nick Arnott last updated

How to test Facebook Chat Heads and stickers for iOS right now, even if they haven't yet been enabled for your account
By Nick Arnott last updated
Viber calling and messaging service hacked, 200 million phone numbers, IDs, IP addresses potentially compromised
By Nick Arnott last updated

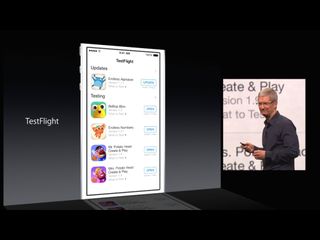
Apple's TestFlight: One year later
By Nick Arnott last updated
It's been almost a year since Apple re-launched TestFlight.

Security Researcher Raises Concerns over Apple's Two-Step Authentication
By Nick Arnott last updated

Apple comments on 'Wirelurker' malware, infected apps already blocked
By Nick Arnott last updated

Second iOS Lock screen bypass discovered, doesn't really expose filesystem
By Nick Arnott last updated
XARA, deconstructed: An in-depth look at OS X and iOS cross-app resource attacks
By Nick Arnott last updated
Does the Indiana University XARA whitepaper make your head hurt? Here's an in-depth look at what "cross-app resource attacks" actually mean for your iOS and OS X systems.