Privacy
Latest about Privacy
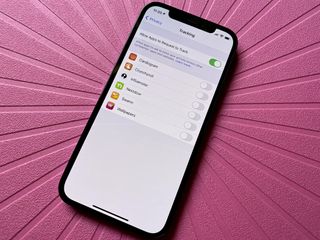
More iPhone users are allowing apps to track them
By Joe Wituschek published
According to new data from Adjust, more users on iOS are opting into app tracking this year than in 2021.
Apple's anti-tracking protections to cost Facebook $10 billion in 2022
By Joe Wituschek published
New data from Lotame project that Facebook will absorb about 80% of the advertising impact from Apple's privacy changes in iOS.

How to watch Tim Cook's speech at the IAPP Global Privacy Summit
By Joe Wituschek published
Tim Cook is this year's keynote speaker at the International Association of Privacy Professionals Global Privacy Summit.

Bloomberg: Apple unknowingly gave customer information to hackers
By Joe Wituschek published
According to a new report from Bloomberg, Apple unknowingly gave customer data to hackers who were masquerading as law enforcement.

Mail on Apple Watch no longer leaks IP addresses with privacy features enabled
By Oliver Haslam published
The newly-released watchOS 8.5 update appears to fix a problem that previously allowed the Mail app on Apple Watches to leak a user's IP address even with Mail Privacy Protection enabled.

MaskerAid is a new app for quickly and easily adding emojis to a photo
By Oliver Haslam published
Have you ever wanted to add an emoji to a photo and found it way more difficult than it ought to be? That's why you need MaskerAid in your life!
Apple privacy chief Erik Neuenschwander gives Data Privacy Day interview
By Stephen Warwick published
Apple privacy chief Erik Neuenschwander has sat down with Rene Ritchie to discuss privacy at Apple.
Apple's working to fix a Safari bug that opens your browsing history up to websites
By Oliver Haslam published
Apple is working on fixing a bug in Safari that could allow websites to see other sites that yuo recently visited.

Woman finds AirTag stuck to her car amid ongoing privacy concerns
By Oliver Haslam published
A woman says she found an AirTag attached to her car after she was alerted that it was moving with her during a drive home from a bar.

Mail on Apple Watch doesn't use Mail Privacy Protection, leaks IP addresses
By Oliver Haslam published
Apple's Mail Privacy Protection system prevents email senders from tracking you when you load remote content in an email. However, that doesn't seem to apply to Mail on Apple Watch.

More than 90 groups want Apple to drop plans to 'build surveillance capabilities' into devices
By Oliver Haslam published

Apple employees express privacy concerns with the company's new child protection features
By Joe Wituschek published
A Slack channel dedicated to the new feature has received over 800 messages, many with concerns about what it means for the future of privacy.

Apple's head of privacy talks about the company's new child abuse detection features in new interview
By Joe Wituschek published
Erik Neuenschwander, Apple's head of privacy, sat down for an interview to talk about the company's new child abuse detection features.
Apple says it's scanning photos to weed out child abusers
By Oliver Haslam last updated
Jane Horvath, Apple’s chief privacy officer spoke at CES 2020 yesterday and confirmed that Apple scans photos to check whether they have any illegal content.
Twitter officially adds support for 'Sign in with Apple'
By Joe Wituschek published
Earlier today, Twitter announced that it was officially rolling out support for Sign in with Apple to iOS users and to web users "soon."

Despite Apple's privacy changes, Facebook posts record ad revenue
By Joe Wituschek published
During Facebook's Q2 earnings call, the company announced advertising revenue of $28 billion, a 56% year-over-year increase.

App Tracking Transparency is decreasing ad revenue by as much as 20%
By Joe Wituschek published
According to Brian Bowman, the CEO of Consumer Acquisition, Apple's stance that ATT is about privacy is "absurd."
Report: iCloud+ Private Relay could spell the end of iOS ad fingerprinting
By Oliver Haslam published
Master your iPhone in minutes
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!

