PayPal, this is the wrong way to do password security
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
You are now subscribed
Your newsletter sign-up was successful
Throughout the week, I frequently work from various cafes around my neighborhood. It's a great way to vary up my scenery and keep my brain on task — and, let's be honest, drink many delicious beverages.
But it also means that cafe Wi-Fi networks, even when accessed through a VPN, can trigger various website security measures. I got one such measure today, when trying to log in to PayPal to check my balance. Unlike many of my accounts, I hadn't turned on two-step authentication for PayPal yet, so all I use to access to my account is a username and password. Instead of seeing PayPal's welcome screen, however, I got this:
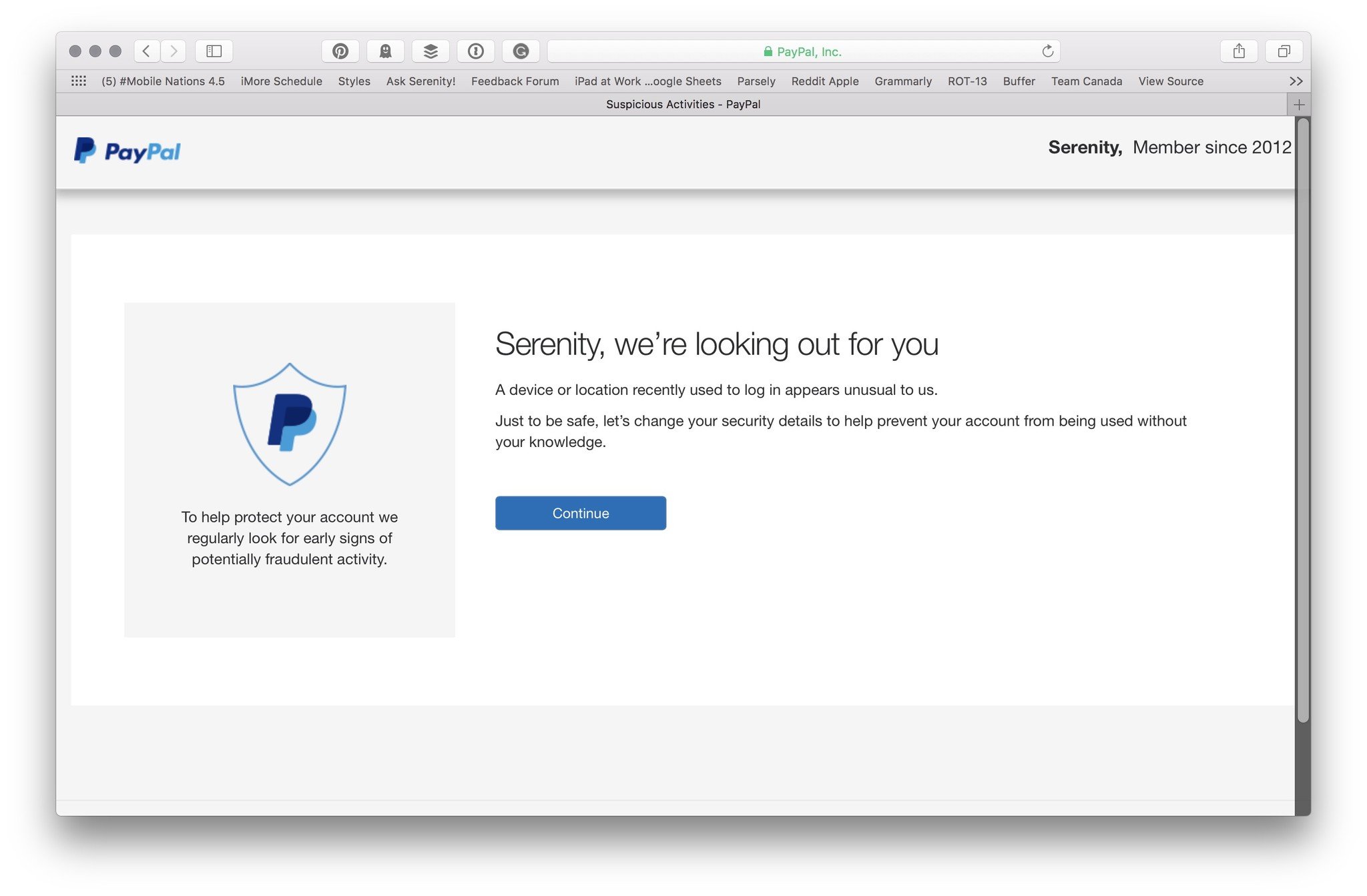
"Serenity, we're looking out for you," the page read after I entered my credentials. Unusual log in, change your security details — not an abnormal warning to get when using a new Wi-Fi network.
What followed, however, was as abnormal a security measure as I'd seen: Rather than have me confirm my identity with a security question, phone call, text message, or emailed link, I was given an immediate password reset form.
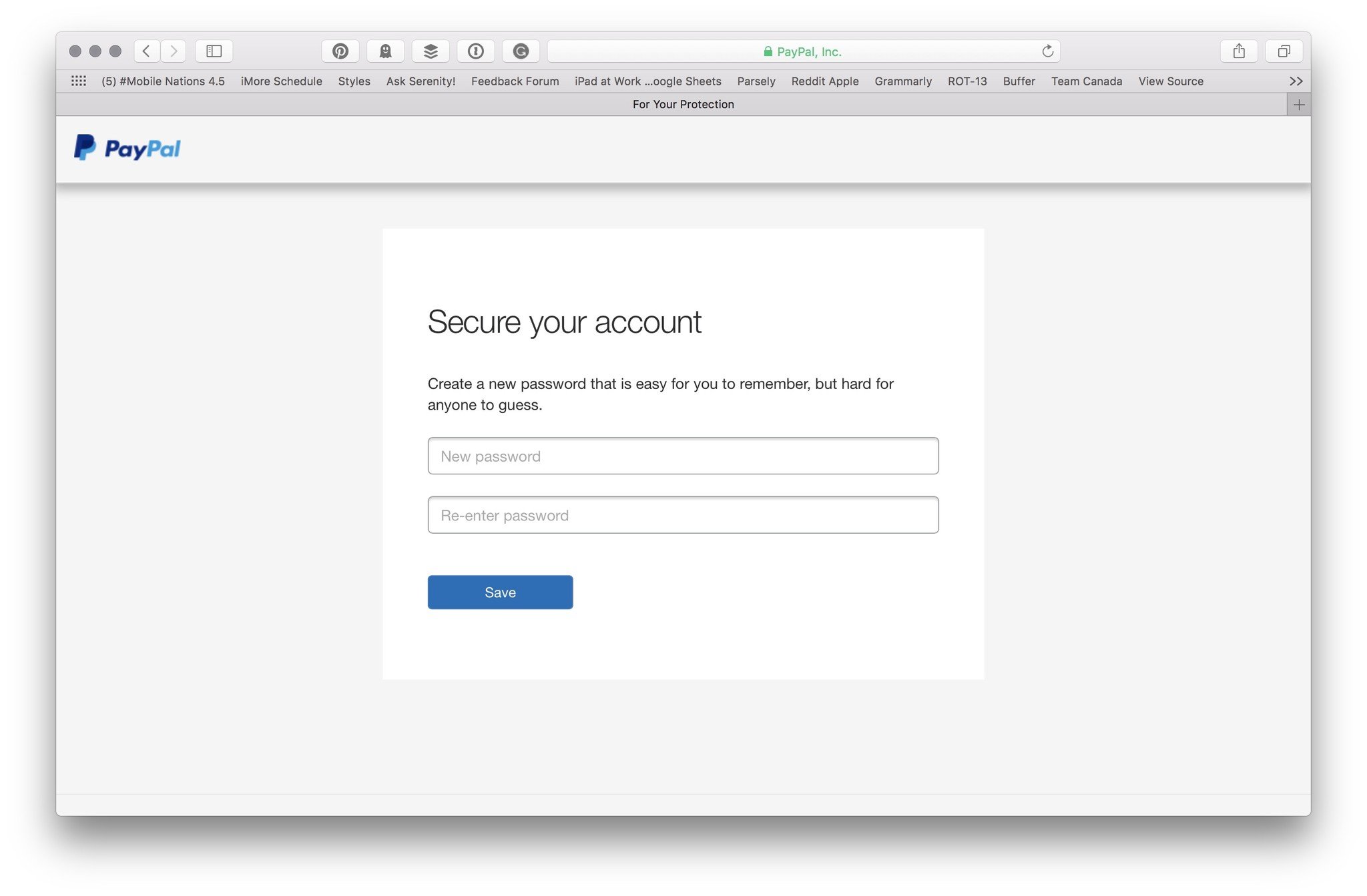
If you know anything about social engineering attacks, your face at this point might look as horrified as mine certainly was upon looking at that form. Contrary to PayPal's goals, this is perhaps the worst way to secure a person's account I can think of: To prompt an immediate password reset — with no secondary identification confirmation — gives a potential attacker an immediate way to cut off access from your account.
Say someone used a social engineering hack to gain access to my PayPal credentials, then logged in with them in a public café: They might get PayPal's note, and then instantly be offered to change my password; my only warning would be a password reset email, and only recourse to call PayPal's consumer support number.
There are many, many better ways to do this: PayPal could ask users to confirm their identity with a second factor of identification, like another device, email account, or phone number; the company could ask you to answer a security question; or it could simply lock the account until you click on a link in your email or text message. None of these options are completely foolproof, but they're a damn sight better than just throwing up a password reset form upon suspicion of malicious activity.
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
Yes, PayPal does offer two-step authentication for users — which would theoretically save you from this warning and password reset —but two-step turns off the service's OneTouch feature; it's also hidden under the label "Security key" and not prominently advertised to its users. And potentially punishing the average person for not turning on two-step isn't fair.
PayPal, let me put it bluntly: This is a crazy, horrifying way to try and secure someone's account. I hope you change it soon; until then, I'm activating two-step on my PayPal account and encourage everyone else to do so ASAP.
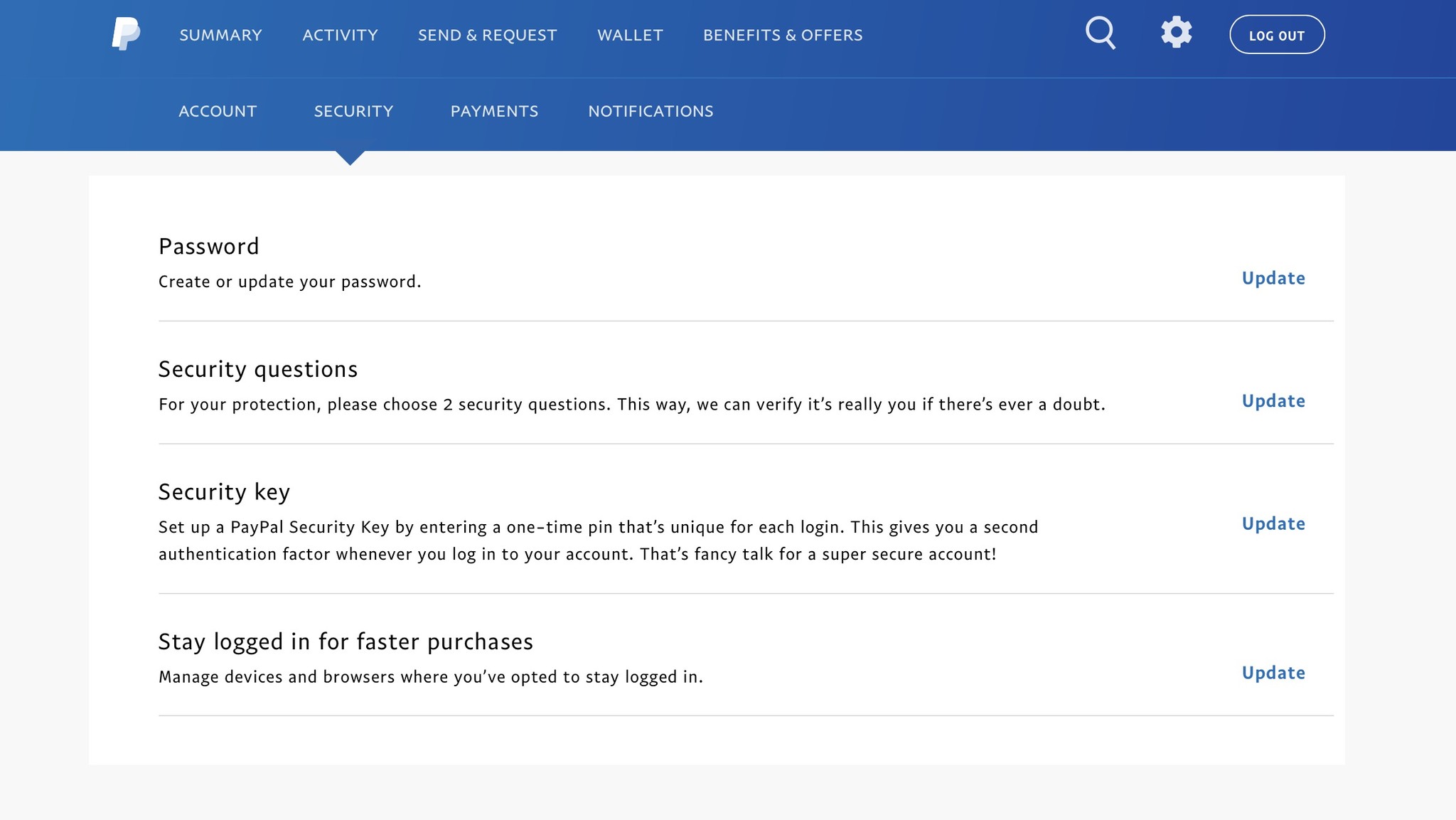
How to turn on two-step authentication for PayPal
- Log in to PayPal.
- Click on the Settings gear icon in the upper right corner.
- Select the Security tab.
- Click on the Update link next to Security Key.
- Register a new phone number.
- Enter the six-digit security code sent to your mobile number.
- Press Done.
Now, whenever you log into PayPal, you'll need a six-digit key from your iPhone to proceed. This will also turn off PayPal's OneTouch feature.
I put in a request to the company's media relations line to find out why PayPal does security in this manner, and will update this story as I find out more.
Serenity was formerly the Managing Editor at iMore, and now works for Apple. She's been talking, writing about, and tinkering with Apple products since she was old enough to double-click. In her spare time, she sketches, sings, and in her secret superhero life, plays roller derby. Follow her on Twitter @settern.

