Phones
Latest about Phones

The Pixel 9 ripped off the iPhone's SOS via satellite feature and that's a good thing
By Joe Wituschek published
Google may be ripping off Apple with the Pixel 9's new SOS via satellite feature, but these features should be on every phone.

Do you need to spend $100 on an iPhone case? I’ve tested hundreds of them, and here’s what you have to consider
By Karen S Freeman published
Luxury cases are still a big part of the iPhone accessory ecosystem. But why would anyone ever want one, and are there any that are actually worth the high price tag?

Apple accused of using blood minerals from a region 'devastated by grave violations of human rights' in its products
By Oliver Haslam published
Congo has accused Apple of using blood minerals and has demanded a response from CEO Tim Cook.
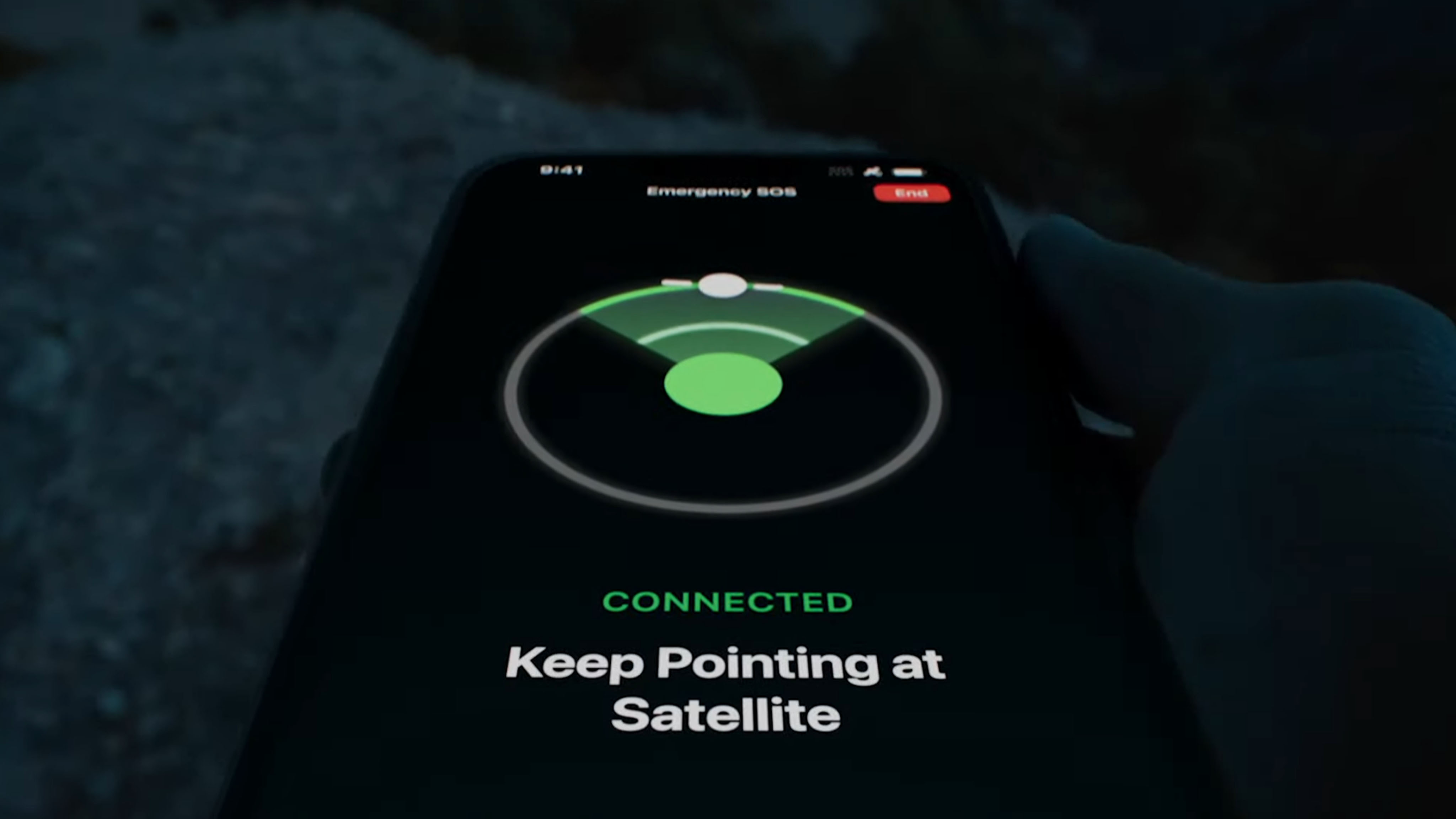
A life-saving iPhone feature could come to Google's next flagship phone when it's unveiled later this year
By Oliver Haslam published
The Google Pixel 9 could be about to borrow a life-saving iPhone 14 feature according to a new report.

Here's your first look at iPhone 16 Pro — Stunning concept shows off a rumored Dynamic Island redesign and a mystery button
By Oliver Haslam published
Rumors suggest Apple is ready to make a big change with the iPhone 16 Pro and this concept shows it off and more.

iPhone 15 Pro's upgrades bag popular 'Best Camera' gong, but it isn't enough to make it the best phone of the year as Google's Pixel 8 triumphs
By Oliver Haslam published
Popular YouTuber Marques Brownlee gave the iPhone 15 Pro his 'Best Camera' award but it was the Google Pixel 8 that took the top honor.

Using the iPhone 15 Plus at Disneyland convinced me it's the best phone for most people
By Tshaka Armstrong published
Opinion Battery life, processing power, and solid cameras make this the best phone for most people — as a demanding Disney trip proved.
Apple's being sued by Venmo and Cash App users over iPhone crypto transfer fees
By Oliver Haslam published
Apple is being sued by users of some finance apps because they aren't allowed to use crypto with them thanks to App Store rules.
Apple could be forced to yank some of the world's most popular apps from the Chinese App Store
By Oliver Haslam published
The Chinese App Store might not have Instagram, Facebook, X, and other apps soon if Apple can't convince the local government to change its mind on new laws.

The biggest 6G test yet just took place, bringing commercial use 'one step closer'
By Stephen Warwick published
LG has announced the successful test of 6G wireless technology, transmitting data over 500 meters in an outdoor urban environment.

Apple's AI efforts 'significantly behind' ChatGPT and years away, top analyst claims
By Oliver Haslam published
Apple's AI work is said to be well behind the competition and any talk of a 2024 announcement seems premature.

Apple pulls ChatGPT-like apps from Chinese App Store as 'socialist values' law nears
By Oliver Haslam published
Apple has reportedly removed more than a hundred ChatGPT-like apps from the Chinese App Store as a new law gets ready to come into force.
Apple threatens to yank FaceTime & iMessage from the UK over 'snooper's charter'
By Oliver Haslam published
Apple says that it would rather remove some encrypted services from the UK rather than give the government a back door into people's devices.
Twitter gains AirPlay support for watching videos on the big screen
By Oliver Haslam published
Twitter now supports AirPlay to make it easier than ever to watch content on the big screen.

One week with the Samsung Galaxy Z Fold 4 and my iPhone love will never be the same again
By Graham Barlow published
Opinion What can Apple learn from a folding phone? It’s a weird flex, but ok.

Two UK networks are merging to create one 5G monster
By Oliver Haslam published
The U.K. carriers Vodafone and Three have announced an intention to merge into one super-carrier.

Five Scandals and two molehill mountains: Apple's "Gate" scandals explained
By Carrie Marshall published
Do you remember where you were when Steve Jobs said you were holding your phone wrong? We do.
Apple's iPhone App Store rules labeled 'absurd' as Elon Musk and Spotify's CEO pile on
By Oliver Haslam published
Spotify CEO Daniel Ek and Twitter owner/CEO Elon Musk have complained about Apple's in-app subscription rules with one calling them "absurd."
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!