Find My: Everything you need to know to track your iPhone, iPad, Mac and more
Whether you’re trying to locate people, your iPhone or your wallet, Find My can help.
When Apple launched Find My iPhone 12 years ago it was a revolutionary idea, if fairly limited in terms of features. The idea was that by using an app on an iOS device, or by logging into iCloud on a computer, you could identify the exact location of an iPhone, iPod, or iPad that was connected to your account. You could then have the device play a sound, lock it with a passcode, or erase all contents and settings on the device if it had been stolen.

This article originally appeared in Mac|Life magazine. If you'd like to stay up-to-date on all the latest news, tips, guides and more for all things iPhone, MacBook, iPads and more, check out the latest subscription deals. Subscribe to the digital edition today from only $1.16 per issue!
A year later, Find My iPhone was joined by Find My Friends, which allowed you to share your location with friends or family members, either temporarily or permanently.
Skip forward a decade and the Find My app is now on Mac, iOS and iPad OS and allows you to track any of those devices, as well as friends and family members, and the newest addition, AirTags. And Find My is now baked deep into iOS and macOS, allowing you to, for example, see friends’ locations in the Messages app, or manage location sharing in Contacts. Perhaps most useful of all, Apple has opened up the Find My network to third-party devices so that developers whose devices are approved by the Find My network accessory programme, part of Made For iPhone (MFi), can connect their devices to the network. That means the device can be tracked in the Find My app, alongside Apple devices.
How to set up and use Find My

Meeting up with friends at a festival? Locate them with Find My
Whether you share your location permanently with family members so you all know where each other are, or temporarily with groups of friends with whom you’re on holiday or plan to meet at a festival, the Find My app is indispensable. By combining data from Wi-Fi, Bluetooth, cellular networks and GPS, the app is able to identify the location of friends who have agreed to share it with you. The Find My app then displays that location on a map.
Rather cleverly, and with privacy in mind, devices that are sharing their location don’t continually report that location to Apple’s servers. Instead, they wait until a request is made from a device with which the device owner has agreed to share and then report the location. The device to which the request was made will then record that location and if another request is made from the same device within two hours, even if the device is off or out of range, will report the most recent location along with a time stamp.
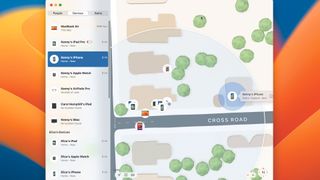
The Find My interface on iPad
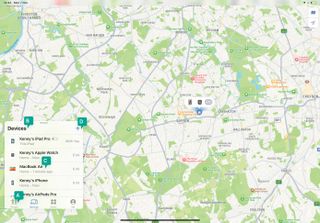
A - What to find
Use these options to choose between locating people, Apple devices, and other items.
Master your iPhone in minutes
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
B - All devices
When you choose Devices, you will see your own devices listed, along with those of family members.
C - Next Steps
Tap a device to play a sound from it, mark it as lost, erase it or set notifictions.
D - Any Extras
Tap the ‘+’ to add AirTag’s or third-party items to the list of devices.
How to locate people and devices with Find My
Share your location on iOS
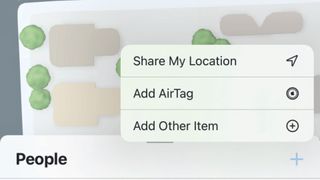
Launch Find My and tap People. Tap the '+' and choose Share My Location. Start typing the name of the person you want to share with and click their name. Tap Send. Choose an option from the menu.
Share your location on Mac
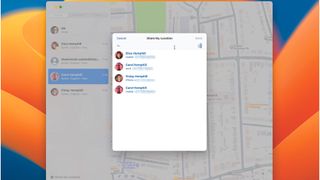
Launch the Mac app and click People at the top left of the window. Click Share My Location at the bottom. Type and select the name of the person. Click Send and choose an option.
Stop sharing
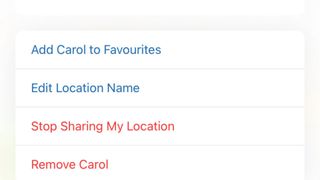
On iPhone or iPad, tap People, then tap the name of the person you want to stop sharing with. Choose Stop Sharing My Location. On Mac, click their name, then click the ‘i’ next to their location and choose the same option.
Find a friend
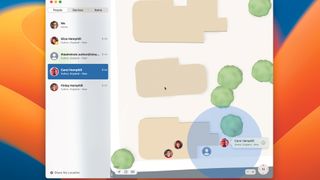
To find the location of someone who is sharing theirs with you, tap or click People, then select that person. When they appear on the map, zoom in by unpinching on iPhone or iPad or clicking the ‘+’ on the Mac.
Get directions

Having a map location is all very well, but if you’re meeting someone, you need to know how to get there. On Mac, Ctrl-click on the person’s name. On iPhone or iPad, tap on it. Choose Directions to open Maps and get directions.
Find My iPhone
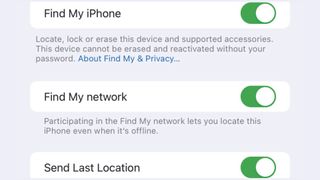
On your iPhone (or iPad or iPod touch), launch the Settings app and tap your name. Choose Find My. Tap Find My iPhone (or iPad or iPod touch). Toggle Find My [device] to On and turn on Find My network.
Locate an iPhone
If you’ve misplaced your iPhone, or you think it’s been stolen, launch Find My on a Mac or iPad signed into the same Apple ID. Tap or click the Devices tab and then tap or click on your iPhone. You’ll see its location.
Find your AirPods
You can also locate missing AirPods and have them play a sound. In the Find My app, tap or click Devices, scroll until you see your AirPods and then tap or click them. Tap or click Left Bud or Right Bud, then Play Sound.
Use in iCloud
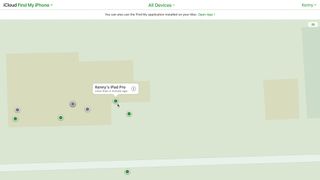
You can access Find My from any computer by logging into your iCloud account. Go to icloud.com in a web browser, sign in and authenticate. Choose Find My iPhone. Click on one of the dots on the map to locate a device.
Do more with Find My
Discover how to add accessories, receive notifications, and more
Locating friends, family members, and your Apple devices using the Find My app is very useful. But Find My has evolved to do much more than that. The latest innovation is that owners of the second generation of AirPods Pro can locate the case separately from the buds themselves, if, for example, they are wearing the buds and can’t find the case.
Even more useful is support for third-party devices through Apple’s Find My network accessory programme. Whether it’s earbuds from Belkin, an e-bike from VanMoof, or tags from Chipolo, you can add them to Find My to keep track of them. So far, the number of accessories that support Find My is limited, but it’s sure to increase in time.
You can mark an iPhone, iPad or Mac as lost and display a message on its screen with a contact number in case it's found. And you can choose to receive notifications when its status changes. Or, if you’re sure it’s been stolen, you can erase its data and settings remotely and lock it with a passcode.
How to mark a device as lost
Locate the device

In the Mac version of Find My, click on Devices at the top of the sidebar. Look for the device and click on it. On iPad or iPhone, tap Devices at the bottom of the screen and then tap on the device you’re looking for.
Select the device
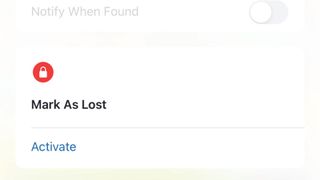
Zoom in on the map if necessary and then click on or tap the device you want to mark as lost. When it is selected, scroll down to Mark as Lost and click or tap Activate. Choose Continue. Type a contact number.
Choose options
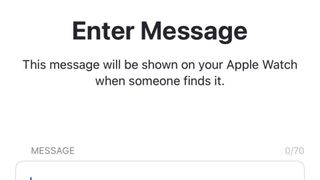
Tap or click Next, then type a message to display on the device. Tap or click Enable to mark the device as lost, then turn on Notify When Found. To turn off Lost mode, use your passcode to unlock the lost device.
How to add other items
Use an AirTag
Remove the battery tab from the AirTag and hold it next to your iPhone, or in Find My, tap Items > Add Item > Add AirTag. When it appears, tap Connect. Choose a name or tap Custom Name. Tap Continue, and again.
Third-party device
Follow the manufacturer’s instructions to prepare the device. Then, in Find My, tap or click Items > Add Item. Tap or click Other Supported Item. Follow the instructions to name and add the device.
Remove a device
To remove a device from Find my, it needs to be offline. So, the first thing to do is turn it off. When it’s offline, launch Find My and locate the device in the Devices list. Tap or click it, then Remove this Device > Remove.
How to manage alerts and notifications
Separation alert
Tap or click Devices or Items. Locate and select the device or item you want to set the alert for. Choose Notify When Left Behind and toggle the option to On. Tap or click New Location to set an exception.
Set a people notification
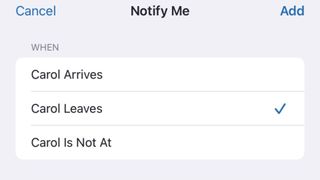
Tap or click People, then select the person you want to set the notification for. Tap or click Add under Notifications and choose an option. Select the options you want, then Add.
Global notifications
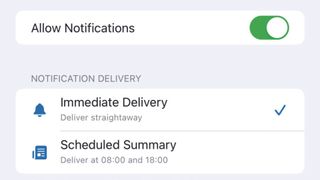
In Settings [System Settings on Mac], choose Notifications then tap Find My. Choose whether notifications should be delivered immediately or scheduled, and how time-sensitive notifications should be delivered.
Tracking alerts
Find out if a Find My device is being used to track you
After much publicity about Apple’s AirTags being used to track people without their knowledge, Apple introduced privacy features to Find My designed to alert you when an unknown device is close by and moving with you. The type of alert differs according to the device. For devices that are registered to someone else’s Apple ID, you will receive a notification with the name of the device. For those that aren’t registered to someone else or that Apple can’t identify, the notification will say ‘unknown device’.
If an AirTag has been tracking you and you don’t have an Apple device in your possession, the AirTag will emit a sound.

John-Anthony Disotto is the How To Editor of iMore, ensuring you can get the most from your Apple products and helping fix things when your technology isn’t behaving itself. Living in Scotland, where he worked for Apple as a technician focused on iOS and iPhone repairs at the Genius Bar, John-Anthony has used the Apple ecosystem for over a decade and prides himself in his ability to complete his Apple Watch activity rings. John-Anthony has previously worked in editorial for collectable TCG websites and graduated from The University of Strathclyde where he won the Scottish Student Journalism Award for Website of the Year as Editor-in-Chief of his university paper. He is also an avid film geek, having previously written film reviews and received the Edinburgh International Film Festival Student Critics award in 2019. John-Anthony also loves to tinker with other non-Apple technology and enjoys playing around with game emulation and Linux on his Steam Deck.
In his spare time, John-Anthony can be found watching any sport under the sun from football to darts, taking the term “Lego house” far too literally as he runs out of space to display any more plastic bricks, or chilling on the couch with his French Bulldog, Kermit.
Most Popular



