Zoom's pre-installation script workaround in macOS 'very shady'
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
You are now subscribed
Your newsletter sign-up was successful
What you need to know
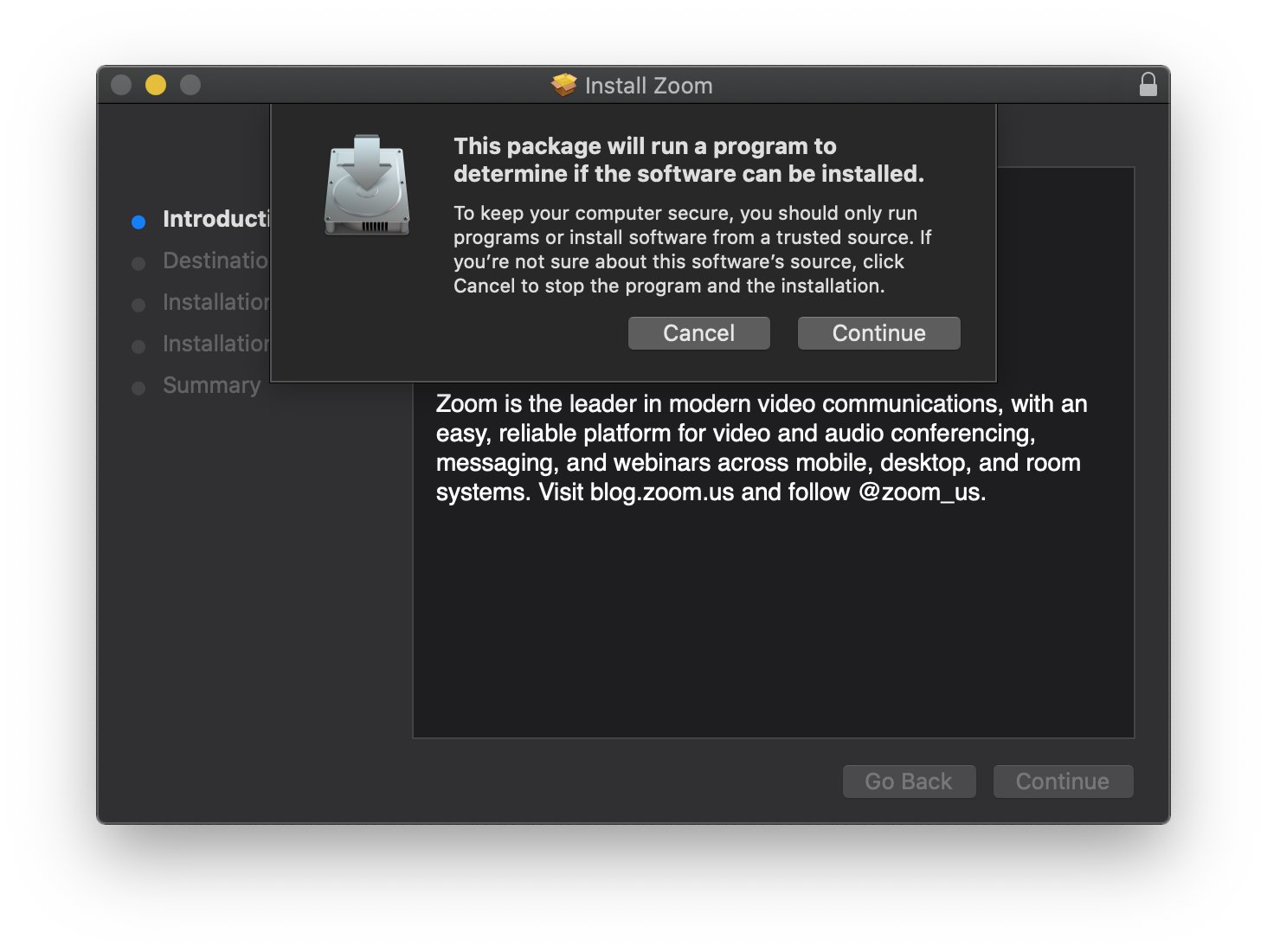
- A malware expert has revealed that video-conferencing app Zoom has "very shady" installation protocols.
- Zoom uses preinstallation scripts to bypass macOS security.
- The finder notes that it's the same trick being used by macOS malware.
In another damning indictment on Zoom's privacy and security practices, a malware expert has revealed that Zoom's macOS installation protocol is "very shady".
In a tweet posted March 30, Twitter user @c1truz_ stated:
Ever wondered how the @zoom_us macOS installer does it's job without you ever clicking install? Turns out they (ab)use preinstallation scripts, manually unpack the app using a bundled 7zip and install it to /Applications if the current user is in the admin group (no root needed).This is not strictly malicious but very shady and definitely leaves a bitter aftertaste. The application is installed without the user giving his final consent and a highly misleading prompt is used to gain root privileges. The same tricks that are being used by macOS malware.
Ever wondered how the @zoom_us macOS installer does it’s job without you ever clicking install? Turns out they (ab)use preinstallation scripts, manually unpack the app using a bundled 7zip and install it to /Applications if the current user is in the admin group (no root needed). pic.twitter.com/qgQ1XdU11MEver wondered how the @zoom_us macOS installer does it’s job without you ever clicking install? Turns out they (ab)use preinstallation scripts, manually unpack the app using a bundled 7zip and install it to /Applications if the current user is in the admin group (no root needed). pic.twitter.com/qgQ1XdU11M— Felix (@c1truz_) March 30, 2020March 30, 2020
The revelation is another mark of Zoom's apparently lax privacy and security practices. The app has risen to prominence following global lockdown and social-distancing measures that have forced many organizations to resort to remote working. Last week it emerged that Zoom was sending data to Facebook even if users didn't have a Facebook account, a problem that has now been fixed.
More recently, it emerged that Zoom calls are not end-to-end encrypted despite claims to the contrary. From that report:
In several instances within Zoom's security white paper, it mentions E2E encryption, and when you enable E2E, you can hover over the green padlock in the top left corner of a meeting and see the popup "Zoom is using an end to end encrypted connection." However, The Intercept claims that when it reached out to Zoom for comment a spokesperson stated:"Currently, it is not possible to enable E2E encryption for Zoom video meetings. Zoom video meetings use a combination of TCP and UDP. TCP connections are made using TLS and UDP connections are encrypted with AES using a key negotiated over a TLS connection."
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!

Stephen Warwick has written about Apple for five years at iMore and previously elsewhere. He covers all of iMore's latest breaking news regarding all of Apple's products and services, both hardware and software. Stephen has interviewed industry experts in a range of fields including finance, litigation, security, and more. He also specializes in curating and reviewing audio hardware and has experience beyond journalism in sound engineering, production, and design.
Before becoming a writer Stephen studied Ancient History at University and also worked at Apple for more than two years. Stephen is also a host on the iMore show, a weekly podcast recorded live that discusses the latest in breaking Apple news, as well as featuring fun trivia about all things Apple. Follow him on Twitter @stephenwarwick9
