Passwords
Latest about Passwords

How to use iCloud Keychain on iPhone and iPad
By James Bentley last updated
iCloud Keychain is a great way to keep track of your passwords, credit cards, and login details, protecting them across devices through iCloud.
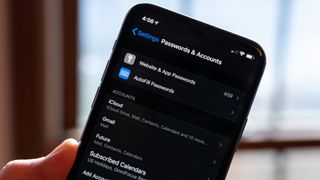
How to look up your accounts and passwords on iPhone and iPad
By Joseph Keller last updated
Looking for your accounts and passwords on your iPhone or iPad? Here's where to find them!
You won't believe what the 88th most popular (and stupid) password of 2022 is
By Oliver Haslam published
A password management company has shared a list of the top 200 most common passwords of the year and it's a worrying read.
How to add notes to your passwords on iPhone and iPad
By Christine Chan published
A new feature has been added in iOS 15.4, allowing you to add notes to passwords in your iCloud Keychain.

Can't unlock your Mac with your Apple Watch? Here's how to fix it!
By Rene Ritchie, Bryan M Wolfe published
If your Apple Watch won't unlock your Mac, here are some fixes you can try!

How to create or remove a passcode on your Apple Watch
By Lory Gil last updated
Don't have a passcode on your Apple Watch? Here's why you should make one!
How to remove a website from Safari's 'Never Save' password list
By Mike Matthews published
Think your Mac's keychain is used only when you want to store a password? Turns out, it's also used when you don't want to store a password.
How passwords work in iOS 12
By Christine Chan published
Throw away your third-party password manager. iOS 12 does all the work for you.

How to generate an app-specific password for Twitter on Mac
By Cella Lao Rousseau published
Looking to generate an app-specific password to really lock down your Twitter account? Here’s how.

How passwords will work in iOS 12
By Joseph Keller published
Passwords are getting a lot of attention in iOS 12. Here’s what you need to know about the upcoming changes.
How to force websites to save passwords to iCloud Keychain in OS X Mavericks
By Allyson Kazmucha last updated
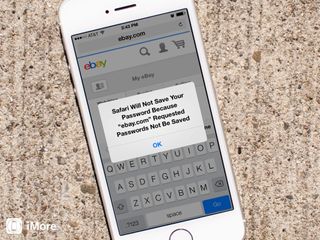
How to force websites to save passwords to iCloud Keychain in iOS 7
By Allyson Kazmucha last updated
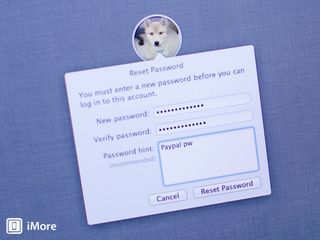
How to reset your Mac desktop password with your Apple ID in OS X Mountain Lion
By Allyson Kazmucha last updated

How to quickly lock your Mac to keep your Chrome passwords safe!
By Allyson Kazmucha last updated

Make your Mac safer online: Five tips for better password security
By Peter Cohen last updated
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!