Apple iCloud+ Private Relay — Explained!
Apple's new Private Relay — part of the also-new iCloud+ subscription service — is not a geo-hop, not a corporate tunnel, and not a VPN. It's a way of protecting your personal information online. But what does any of that even mean?
Why the web isn't private
You're just itching to get the latest, shwayest bobblehead on the web. But as you're busily browsing the reseller site, they're busily creeping on your IP address, your connection ID to the internet, and resolving that to your approximate location. So now they know your IP and your city and that you're into bobbleheads.
But wait, there's more! Because data brokers just love to buy and sell your behavior across the internet. So, through those exchanges, they and everyone else brokering your data are basically following you around digitally, spying on you like… just the worst private dick — as in detective — from the cheesiest of film noir flicks.
Tracking your computer, your city, your interest in bobbleheads at that specific date and time, as well as other sites you visit from that IP. Maybe for your photography hobby. Or even penchant for Pokemon-themed pr0n. And, I mean, zero judgment. You Pikachu you!
Maybe a camera site got your email and physical address when you ordered that last lens. And that email lets them link your work IP to your profile, where they can see you bought a fancy new OLED TV and Video Streaming++ subscription and keep ordering Burritoville for lunch even though you keep visiting local gym sites and never signing up. But that Swipe-right for Vulcans geek dating app, yeah, they live long and prospered all the data out that that.
They even brokered your credit cards, so they know about those pit-stops at Slurpy Burger on the way home every day.
Because Shadow Profiles are TIGHT!
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
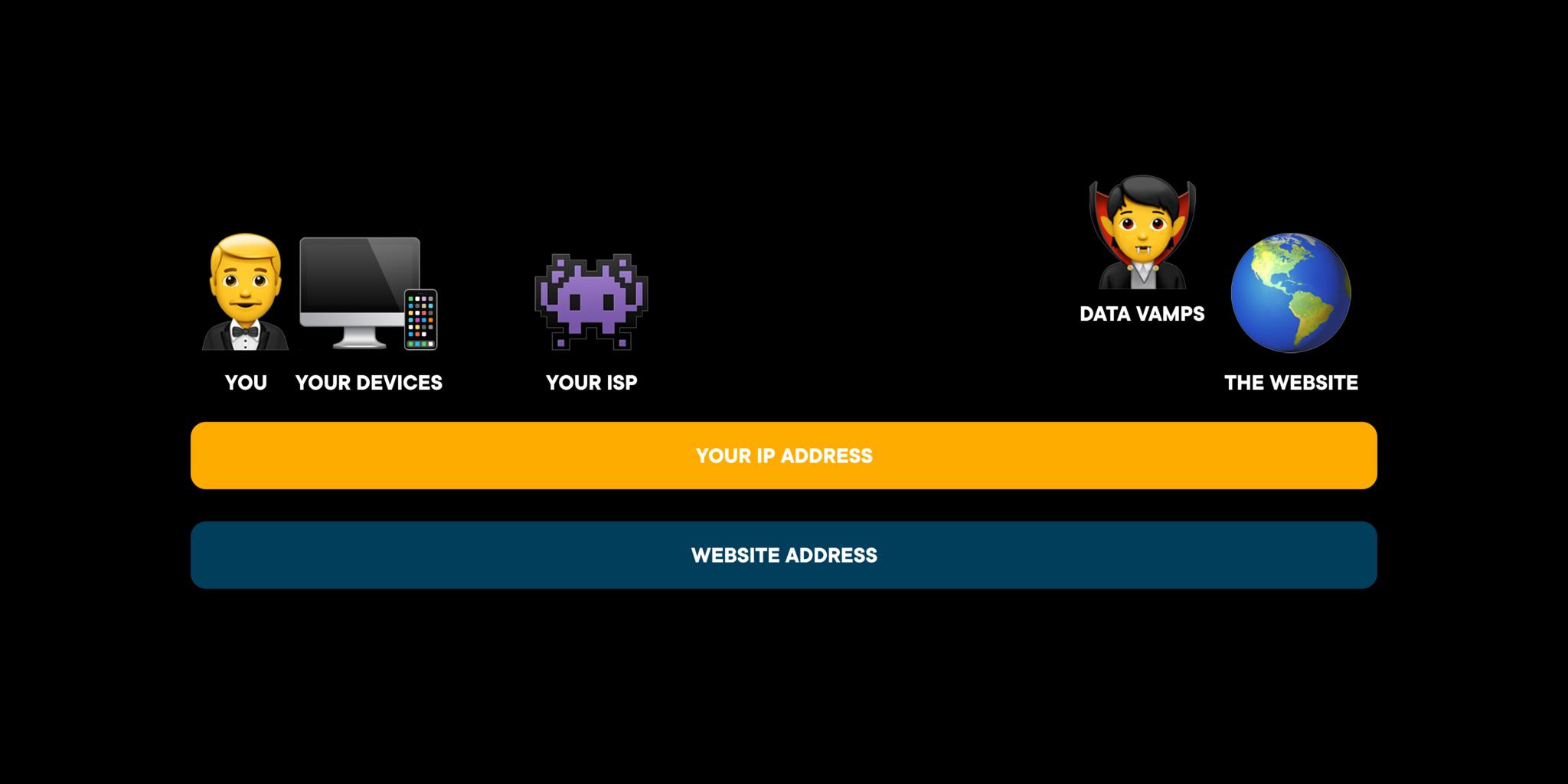
So all this personal information about you, information that you never chose to share with all these companies and never consented to have stored on all their — sometimes extremely hackable — servers, can then be… innocuously used to serve you personalized ads for more bobbleheads or lenses or burgers, but can less innocuously, more egregiously be used to target us with political ads, extremism, conspiracy, and other forms of algorithmic malfeasance. Or, sure, a catalog of Pikachu onesies sent to your door…
Of course, your internet service provider, maybe the maker of your smart router, certainly any public Wi-Fi service you're connecting to or being person-in-the-middled on…
Enter Apple Private Relay
All of this is why Apple's introducing iCloud Private Relay as part of their new subscription iCloud+ service. Subscription because, as you'll see, they're not just using Apple resources for it, but specifically paying for non-Apple resources to make it work privately and securely as well.
Now, Apple is very, very careful not to call Private Relay a VPN or virtual private network, the kind of service you see sponsoring so many videos so always. Because it doesn't do the same exact things as a VPN.
For example, you can't use Private Relay to geo-hop and watch Netflix France or Hulu in the U.S. It's not going to work to securely tunnel into your corporate network to… Yellow restore the internal software build on your Orange xPhone.
What Private relay will do, what it's designed to do, is encrypt all your connections, including any legacy connections not using HTTPS, to obfuscate your real IP address, and to prevent anyone, even Apple, from knowing both who you are and where you're connecting to on the web.
In other words, it's the privacy, dammit.
How Private Relay works

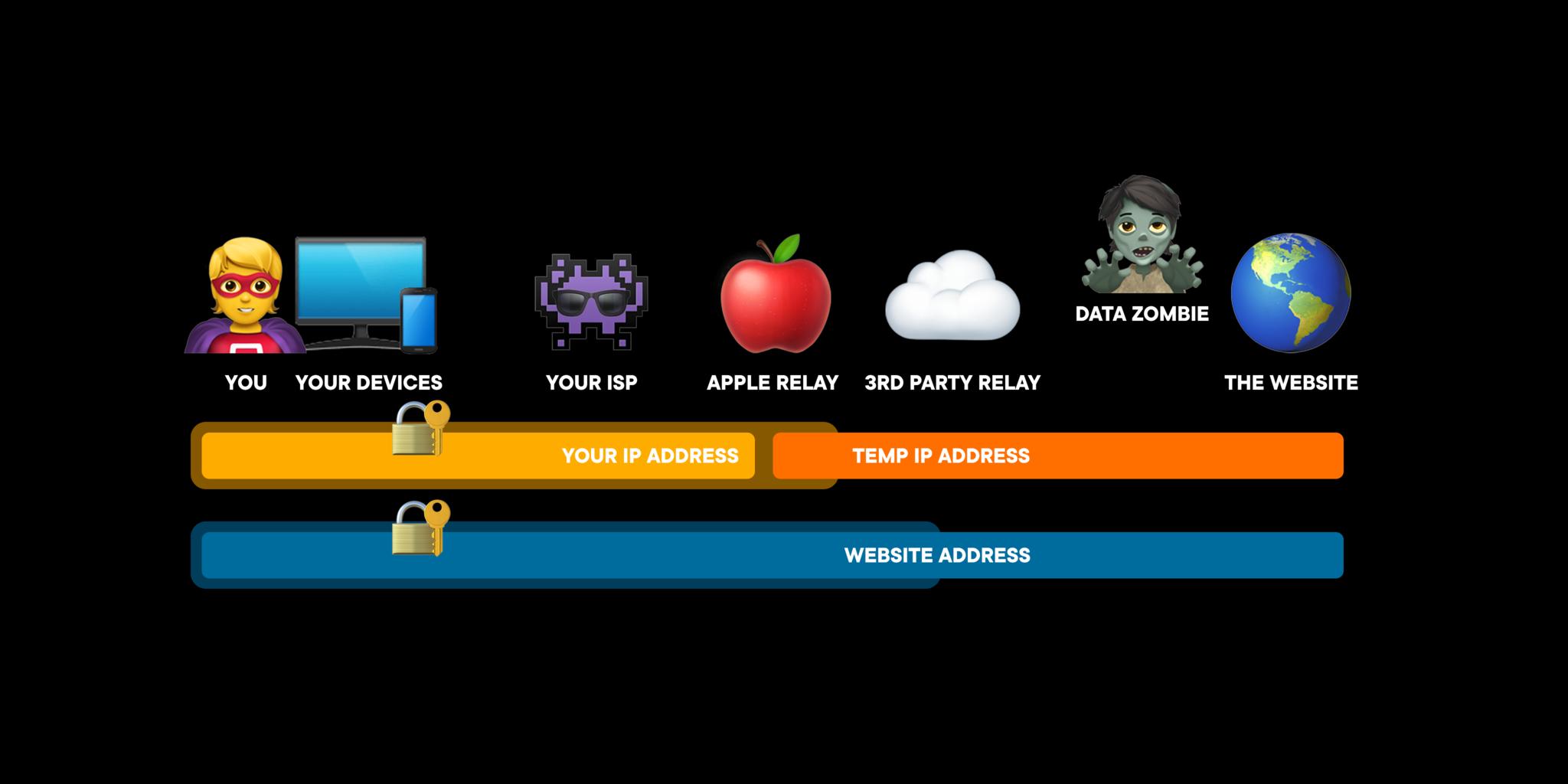
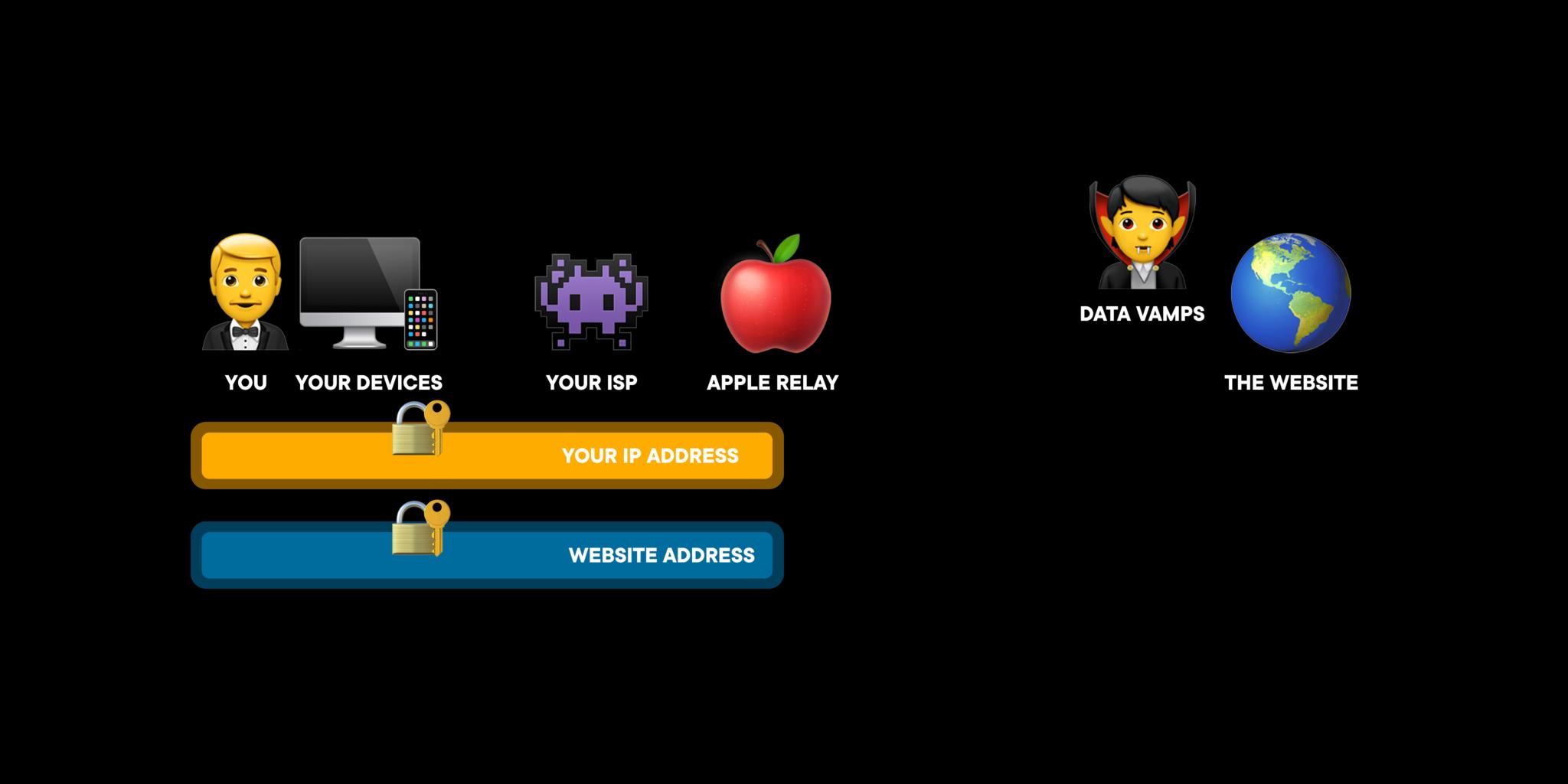
So, now, when you're browsing for that latest, shwayest bobblehead online, your connection to that website using cryptographic binding encryption on your device, then relayed to Apple's ingress proxy server.
Apple uses an RSA-bound access token that's not linkable back to you and a public/private key system to verify your access to the ingress proxy server.
The connection uses QUIC, which is meant to be like TCP but with lower latency and HTTP/3, and because Apple encrypts the connection, even your ISP can't see where it is on the web you want to go. All they see is the connection to Apple's ingress proxy server. So, Apple knows your IP, but not the website you want to go to because that's encrypted.
At that point, Apple will strip away your real IP address and replace it with a temporary IP address from a pool of available addresses. This can be a local IP address, if you still want to be able to get local services or search results, for nearby Slurpy Burgers, for example, or a rando IP where the most someone will be able to get from it is your country or region.
In iCloud Internet Privacy settings, you can switch between Maintain General Location or Use Country and Time Zone for the temporary IP at any time.
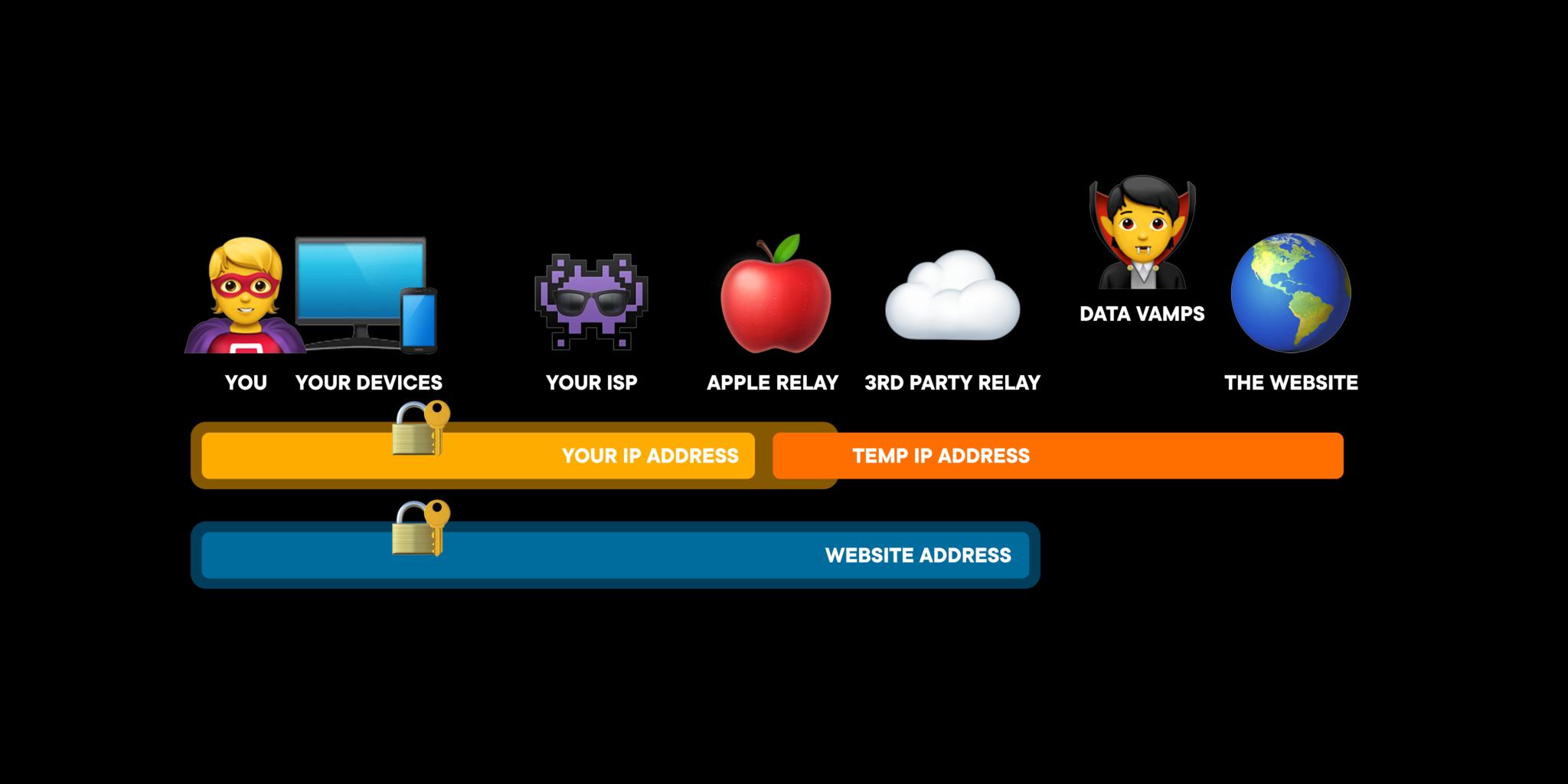
Apple then forwards your connection on to a second relay, an egress proxy server. That server isn't owned by Apple. So it could be… Cloudflare or something similar. There are a bunch of different egress proxy servers and a token-based system to randomly assign them, which is like another layer in the privacy sammich.
The idea is Oblivious DoH, a DNS standard proposed by Apple, Cloudflare, and fastly to decouple IP addresses and queries for… better privacy.

Because the egress relay only gets the temporary IP address from Apple, it has no idea who you are. But, because it has the public key to decrypt the website you're connecting to, it knows where you want to go.
That's worth repeating: Your ISP and Apple's ingress proxy server only knows your IP, not the website you're going to. The third-party egress proxy server only knows the website you're going to, not the IP address you come from. And neither does that website. So no one is left with the complete, end-to-end knowledge necessary to profile you.
Because the temporary IP addresses are from a pool, they can and will be used and re-used by different connections from different people over time, making any data correlations attempted from them… especially useless.
Now, the advantage is that shadow profiles will be much harder to compile and update. Hopefully, much, much harder.
Private Relay pros and cons
Because Private Relay is currently focused on Safari browsing, DNS queries, and only a small subset of previous insecure app traffic over port 80, if you use a browser like Chrome, Google will probably still have perfect knowledge of everything you do, or if you're logged in to Facebook or YouTube or Amazon, they'll still have complete first-party knowledge of what you do on their properties, and depending on your tracking settings, what you do across other sites and apps as well.
Also, in order to function as intended, parental control apps, VPN, Proxy apps, and similar won't be affected by Private Relay.
If you're not logged in, obfuscating your IP address will affect things like watch and browse history, so maybe YouTube counts your repeated views of the same video but doesn't attribute your viewing of multiple videos. Or, if someone is engaging in annoying or abusive behavior, using IP blocking may no longer be an effective way to stop them. Machine learning systems and other technologies, similar to the anonymized ad attribution APIs Apple's been adding over the years, will have to pick up that a-hole prevention slack.
But at least you'll be spared your roommate ever asking about that Pikachu onesie catalog!

Rene Ritchie is one of the most respected Apple analysts in the business, reaching a combined audience of over 40 million readers a month. His YouTube channel, Vector, has over 90 thousand subscribers and 14 million views and his podcasts, including Debug, have been downloaded over 20 million times. He also regularly co-hosts MacBreak Weekly for the TWiT network and co-hosted CES Live! and Talk Mobile. Based in Montreal, Rene is a former director of product marketing, web developer, and graphic designer. He's authored several books and appeared on numerous television and radio segments to discuss Apple and the technology industry. When not working, he likes to cook, grapple, and spend time with his friends and family.
