High Sierra will regularly check your Mac’s firmware for anomalies
The newest macOS update, High Sierra, will be available later today, and with it will come a new security feature: your Mac will now run weekly checks on its EFI firmware automatically. One of the engineers responsible, Xeno Kovah, explained how the process works in a series of tweets that have since been deleted, but luckily Mac blog The Eclectic Light Company caught them and recapped them pretty concisely:
The new utility eficheck, located in /usr/libexec/firmwarecheckers/eficheck, runs automatically once a week. It checks that Mac's firmware against Apple's database of what is known to be good. If it passes, you will see nothing of this, but if there are discrepancies, you will be invited to send a report to Apple.
Essentially this means that Apple has a database of this "known good" data, and it compares your current EFI firmware data with this. If there are any fishy inconsistencies that suggest your data may have been messed with in some way, your system will alert you with an error message that looks like this:
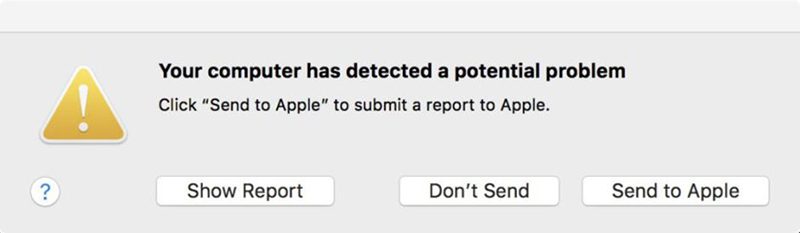
If you send your data, which Kovah strongly suggests, Apple will analyze it to confirm whether or not it's been compromised. This is all done in true Apple fashion — the data you send will be stripped of any info stored in NVRAM in order to maintain the company's commitment to protecting user privacy. If Apple doesn't see any harmful alterations in your sent firmware data, then it will update its "known good" database accordingly.
Thoughts? Questions?
How do you feel about High Sierra's new security feature? Let us know in the comments.
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
Tory Foulk is a writer at Mobile Nations. She lives at the intersection of technology and sorcery and enjoys radio, bees, and houses in small towns. When she isn't working on articles, you'll likely find her listening to her favorite podcasts in a carefully curated blanket nest. You can follow her on Twitter at @tsfoulk.

