Breaking into a MacBook requires you as an accomplice
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
You are now subscribed
Your newsletter sign-up was successful
Joanna Stern's combo video/columns were the inspiration for my own VECTOR series, so I watch/read everything she does. Especially when that everything includes security in general and Apple security in specific.
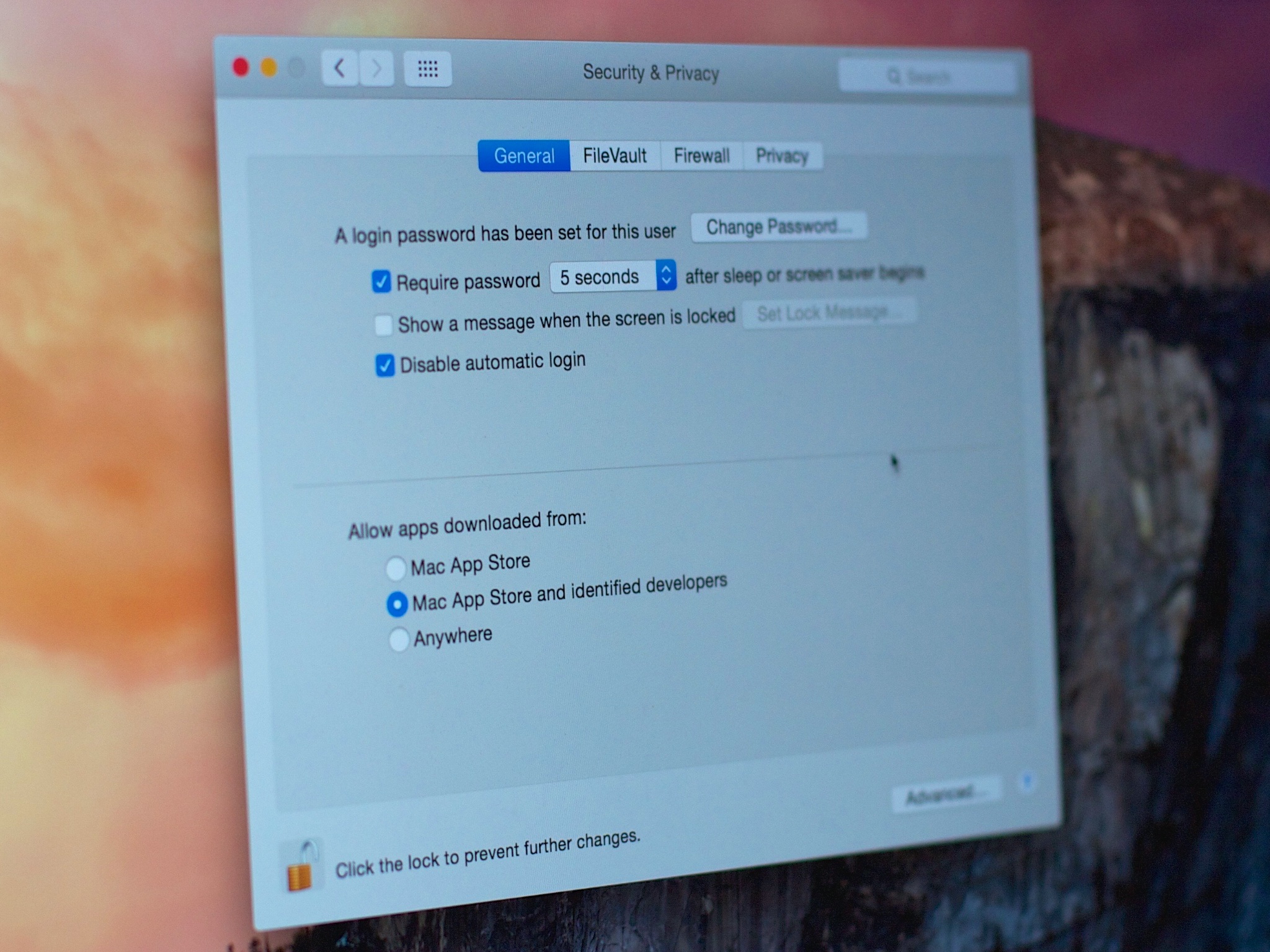
Hacking a 2015 MacBook Air running the latest MacOS version, Mojave, also required a multistep process (and some missteps by the "victim"). This time the malware was embedded in an .odt document, an open-source file format.
The process basically requires the attacker to trick you into turning off multiple layers of both OS and app-level security. So much so that it might as well be a Jedi mind-trick of coercion.
Sure, there will always be bugs and fixes to those bugs, but it's typically the humans that compromise the systems, and the best thing any and all of us can do is refuse to be that compromise.
Even the simplest and most basic best practices would render the attacks Joanna describes useless, so make sure you inform and empower everyone you know, so they'll know to never turn off the built-in protections.
Also: Yes, burn trash IP cameras. With fire.
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!

Rene Ritchie is one of the most respected Apple analysts in the business, reaching a combined audience of over 40 million readers a month. His YouTube channel, Vector, has over 90 thousand subscribers and 14 million views and his podcasts, including Debug, have been downloaded over 20 million times. He also regularly co-hosts MacBreak Weekly for the TWiT network and co-hosted CES Live! and Talk Mobile. Based in Montreal, Rene is a former director of product marketing, web developer, and graphic designer. He's authored several books and appeared on numerous television and radio segments to discuss Apple and the technology industry. When not working, he likes to cook, grapple, and spend time with his friends and family.
