iOS VPN bug can lead to user data and IP addresses being leaked
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
You are now subscribed
Your newsletter sign-up was successful
What you need to know
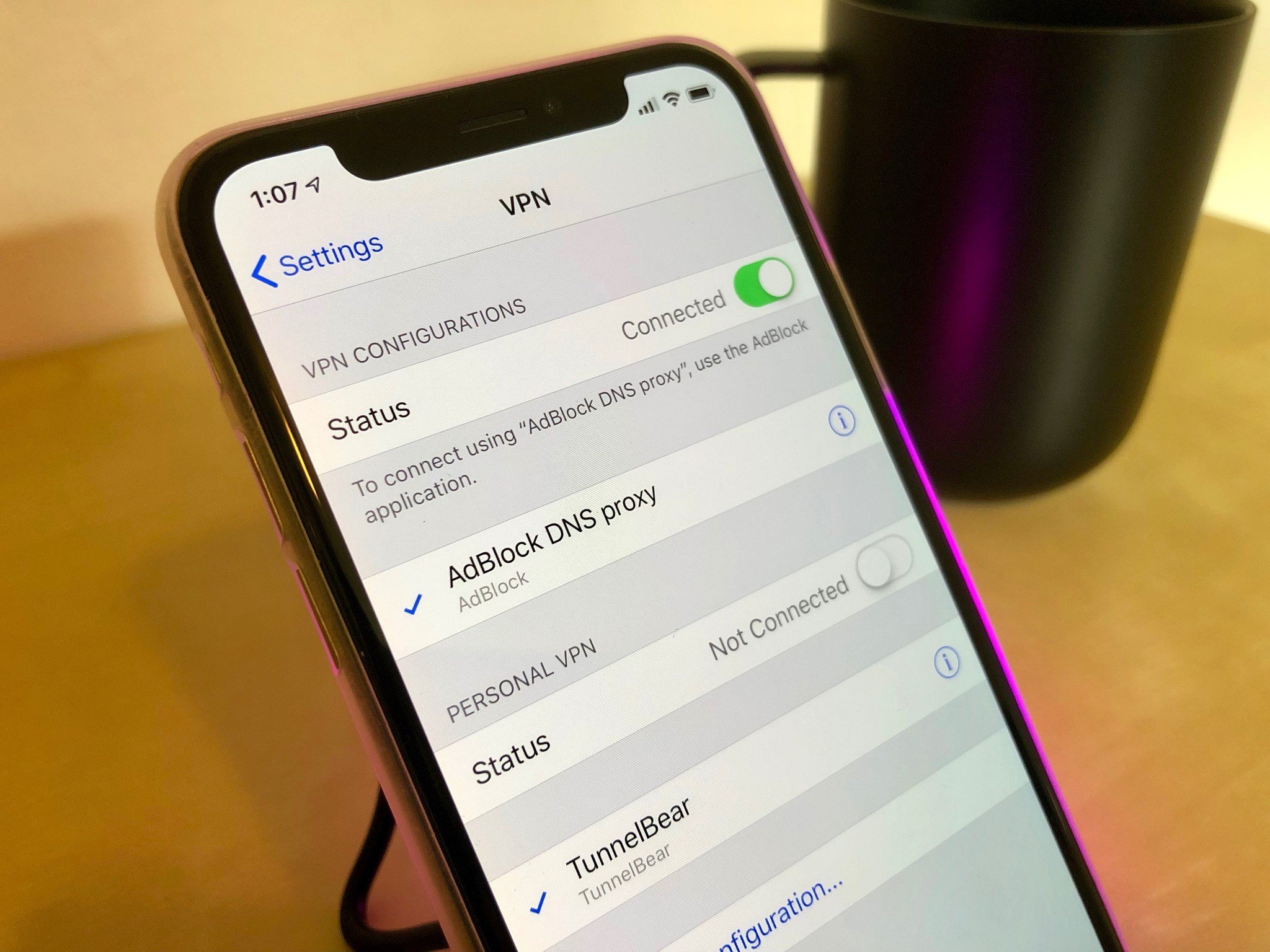
- There appears to be a bug affecting VPN security on iOS.
- It was discoverd by ProtonVPN in iOS 13.3.1 or later.
- The issue could lead to a user's data or IP address being leaked.
A report from Bleeping Computer claims that there's an unpatched vulnerability in iOS VPN security that could lead to user data or IP addresses being leaked.
According to the report:
A currently unpatched security vulnerability affecting iOS 13.3.1 or later prevents virtual private networks (VPNs) from encrypting all traffic and can lead to some Internet connections bypassing VPN encryption to expose users' data or leak their IP addresses.While connections made after connecting to a VPN on your iOS device are not affected by this bug, all previously established connections will remain outside the VPN's secure tunnel as ProtonVPN disclosed.This VPN bypass vulnerability (rated with a 5.3 CVSS v3.1 base score) was discovered by a security consultant part of the Proton community and was disclosed by ProtonVPN to make users and other VPN providers aware of the issue.
Apparently, iOS is not terminating all existing internet connection when the user connects to a VPN. These connections are automatically reestablished after the VPN tunnel is set up. According to finder Proton VPN:
"Most connections are short-lived and will eventually be re-established through the VPN tunnel on their own... However, some are long-lasting and can remain open for minutes to hours outside the VPN tunnel."
According to the findings, user data could be exposed to third parties, or your IP address could be leaked, potentially revealing your location or exposing both the user and destination servers to attacks.
ProtonVPN has shared the findings with Apple, which has acknowledged the problem and "is currently looking into options on how to fully mitigate it." In the meantime, it's recommended that users use 'Always-on VPN' to avoid the issue, however, this does not work for third-party VPNs.
For third-party VPNs they recommend the following:
- Connect to a VPN server.
- Turn on airplane mode. This will kill all Internet connections and temporarily disconnect the VPN.
- Turn off airplane mode. The VPN will reconnect, and your other connections should also reconnect inside the VPN tunnel (not 100% reliable)
We test and review VPN services in the context of legal recreational uses. For example:
1. Accessing a service from another country (subject to the terms and conditions of that service).
2. Protecting your online security and strengthening your online privacy when abroad.
We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!

Stephen Warwick has written about Apple for five years at iMore and previously elsewhere. He covers all of iMore's latest breaking news regarding all of Apple's products and services, both hardware and software. Stephen has interviewed industry experts in a range of fields including finance, litigation, security, and more. He also specializes in curating and reviewing audio hardware and has experience beyond journalism in sound engineering, production, and design.
Before becoming a writer Stephen studied Ancient History at University and also worked at Apple for more than two years. Stephen is also a host on the iMore show, a weekly podcast recorded live that discusses the latest in breaking Apple news, as well as featuring fun trivia about all things Apple. Follow him on Twitter @stephenwarwick9
