An iOS vulnerability may have been exploited to spy on China's Uyghur population
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- An iOS exploit might have been used to spy on China's Uyghur population.
- That's according to a report from security company Volexity.
- It uses an exploit to target a WebKit vulnerability previously thought patched, to implant malicious software on a device.
A report from cybersecurity company Volexity claims an iOS exploit may have been used to target China's Uyghur population with malicious spying software.
According to the report, a series of attacks against Uyghurs were uncovered dating back to September 2019 from "multiple Chinese APT actors", one of which Volexity calls 'Evil Eye.' That involved launching an exploit to install malware on Android Phones and iOS devices. It was spotted by Volexity, addressed by Google, and then went quiet. Volexity now says that a new strand of attack has emerged:
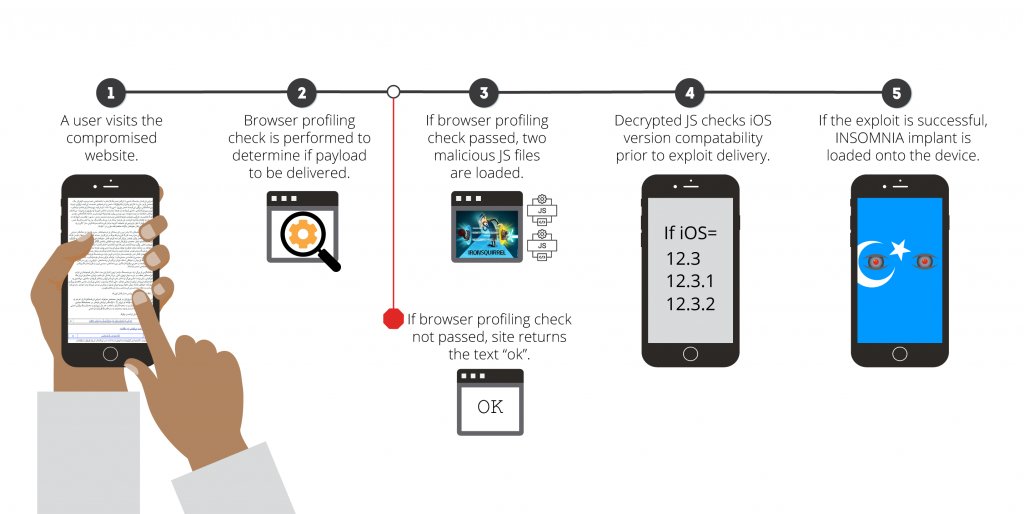
This largely remained the case until early January 2020, when Volexity observed a series of new activity across multiple previously compromised Uyghur websites.In the latest activity identified by Volexity, the Evil Eye threat actor used an open-source framework called IRONSQUIRREL to launch their exploit chain. The exploits used targeted Apple iOS operating systems leveraging a vulnerability in WebKit that appears to have been patched in the summer of 2019. The exploit works against iOS versions 12.3, 12.3.1, and 12.3.2. These versions of iOS are newer than anything mentioned in the Google Project Zero blog, or any other recently published reports involving weaponized exploits that can be used remotely against iPhones or iPads. If the exploit is successful, a new version of the implant described by Google will be installed onto the device. Volexity refers to this implant by the name INSOMNIA.
Whilst Volexity notes that "the first round of attacks were identified across several websites", it says that "future attacks were only observed in conjunction with the Uyghur Academy website." That is, to say that these attacks, wherever they come from, are targeted at the ethnic minority. The exploit works as per the above diagram:
- A user visits the compromised website
- A browser profiling check is performed to determine if the payload is to be delivered
- If the check passes, two malicious JS files are loaded
- Decrypted JS checks iOS version compatibility prior to delivery of the exploit
- If the exploit is successful, INSOMNIA implant is loaded onto the device
In conclusion, the report states:
Even though the vulnerabilities exploited in this report are patched as of July 2019 with iOS version 12.4 and newer, it appears that Evil Eye is likely having success with these attacks. According to Apple's own statistics from its website:
- 43% of iPad devices using the App store use iOS 12 or earlier
- 30% of iPhone devices using the App store use iOS 12 or earlier
This represents a considerable attack surface of potentially vulnerable devices.
The report further notes:
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
It can now be confirmed that in the past six months, Uyghur sites have led to malware for all major platforms, representing a considerable development and upkeep effort by the attackers to spy on the Uyghur population.

Stephen Warwick has written about Apple for five years at iMore and previously elsewhere. He covers all of iMore's latest breaking news regarding all of Apple's products and services, both hardware and software. Stephen has interviewed industry experts in a range of fields including finance, litigation, security, and more. He also specializes in curating and reviewing audio hardware and has experience beyond journalism in sound engineering, production, and design.
Before becoming a writer Stephen studied Ancient History at University and also worked at Apple for more than two years. Stephen is also a host on the iMore show, a weekly podcast recorded live that discusses the latest in breaking Apple news, as well as featuring fun trivia about all things Apple. Follow him on Twitter @stephenwarwick9
