WhatsApp is getting a privacy feature it should already have
What you need to know
- WhatsApp is working on a new privacy feature.
- A future update should prevent people from seeing when you're online.
- This feature has long been a heavily requested one.
WhatsApp is working on a new feature that will allow people to hide their online status from everyone, a feature that it should arguably have had for some time now.
The vital privacy improvement is now being developed according to a WABetaInfo report, although it isn't yet ready for beta testing let alone release to the App Store.
With the new feature enabled, users will have more control over who can see when they are actively using WhatsApp, something that isn't currently offered. It's also a feature that users have been requesting for some time now.
As you can see in this screenshot, it will be possible to configure who can see when we are online right within our last seen settings thanks to two new options: "Everyone" and "Same as Last Seen". For example, if you choose "My contacts" for "Last Seen" and "Same as Last Seen" for "online", it means non-contacts won't be able to see when you're online.
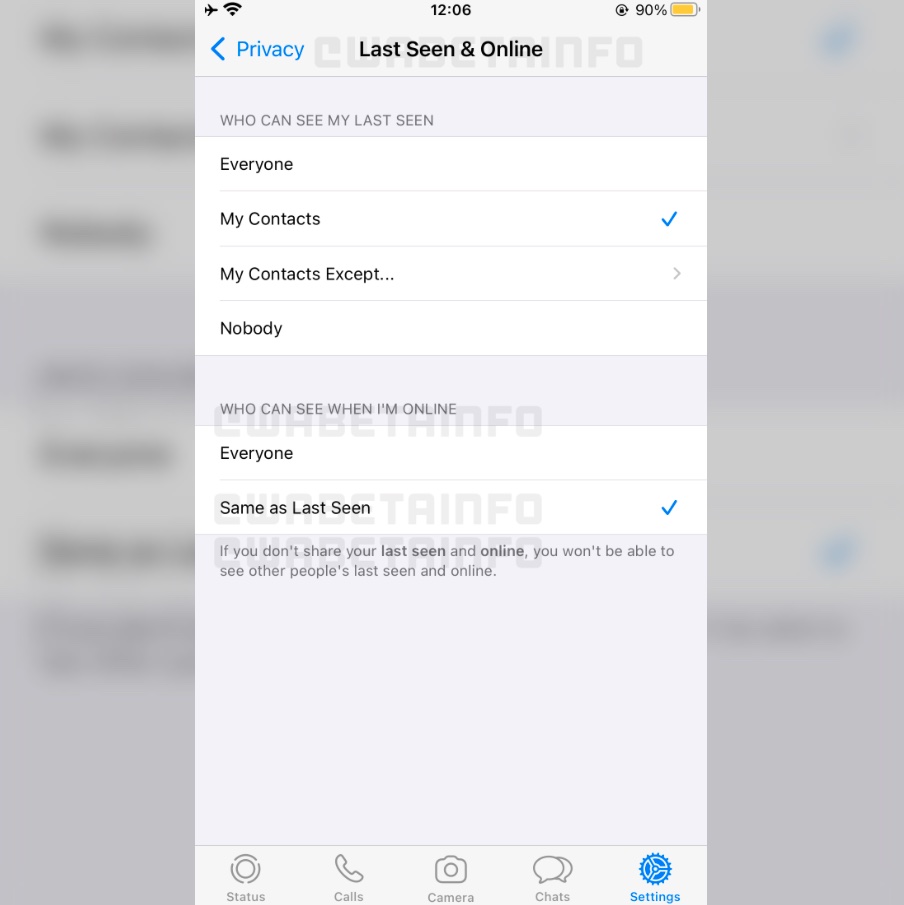
WhatsApp already prevents people you don't know from seeing your Last Seen information, but that's no good for people who want to hide their online status entirely. This new change, once implemented, will deal with that once and for all.
Unfortunately, there is no telling when one of the best iPhone instant messaging apps will gain a vital privacy feature that should already be there. Hopefully it's one that won't take too much development and is available sooner rather than later.
Those who don't yet have WhatsApp installed can download it from the App Store for free right now. It's a great tool for staying in touch with friends and family who use Android devices — although it's probably time you get them to switch to iPhone instead!
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!

Oliver Haslam has written about Apple and the wider technology business for more than a decade with bylines on How-To Geek, PC Mag, iDownloadBlog, and many more. He has also been published in print for Macworld, including cover stories. At iMore, Oliver is involved in daily news coverage and, not being short of opinions, has been known to 'explain' those thoughts in more detail, too.
Having grown up using PCs and spending far too much money on graphics card and flashy RAM, Oliver switched to the Mac with a G5 iMac and hasn't looked back. Since then he's seen the growth of the smartphone world, backed by iPhone, and new product categories come and go. Current expertise includes iOS, macOS, streaming services, and pretty much anything that has a battery or plugs into a wall. Oliver also covers mobile gaming for iMore, with Apple Arcade a particular focus. He's been gaming since the Atari 2600 days and still struggles to comprehend the fact he can play console quality titles on his pocket computer.
