Mysk: Link previews in messaging apps could share your location, expose data to third parties
What you need to know
- New research raises concerns about how messaging apps handle link previews.
- Some apps could be leaking your location to third parties.
- Files you share could also be accessible by other people and companies, too.
New security research by Talal Haj Bakry and Tommy Mysk has found that some messaging apps are mishandling data, potentially sharing details like your IP address and location with third parties. Files that you send could also end up on a third-party's server as well.
On top of all that, link previous could also download multiple gigabytes of data if the link takes a messaging app to a large file.
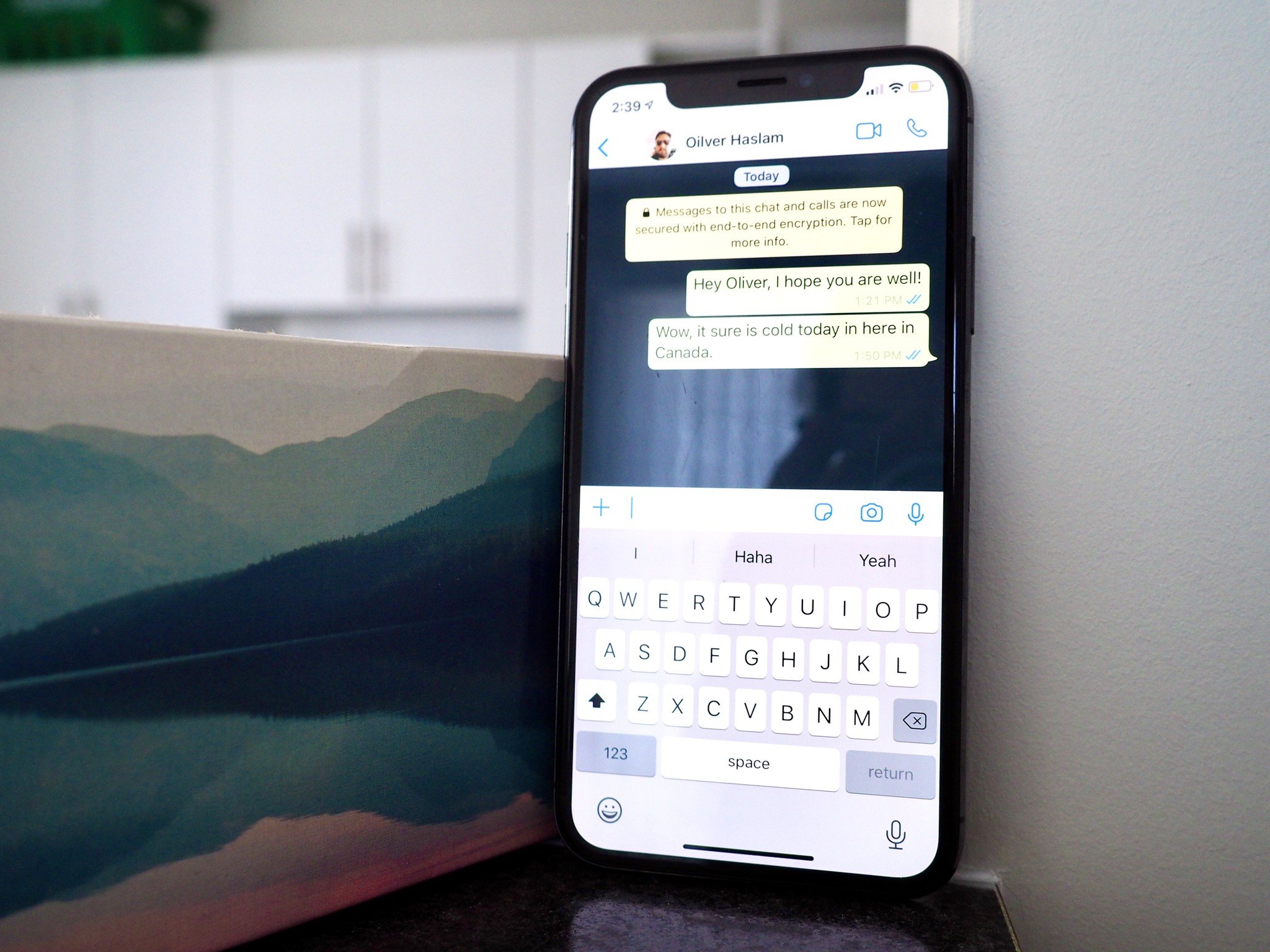
Link previews give the person receiving a URL a glimpse of what they will see if they tap on it. But that preview needs to be generated and if it's the receiver doing it, it could be happening on a server somewhere. And it's there where the data leak can happen.
Link previews in chat apps can cause serious privacy problems if not done properly. We found several cases of apps with vulnerabilities such as: leaking IP addresses, exposing links sent in end-to-end encrypted chats, and unnecessarily downloading gigabytes of data quietly in the background.
The researchers tested a number of popular and high-profile messaging apps and services including Discord, Google Hangouts, Instagram, Slack, Zoom, and iMessage. Some fared better than others with one in particular, LINE, behaving particularly badly. While it offers end-to-end encryption on its messages, it still sends links to a server for the preview to be generated. Effectively undoing the encryption.
Well, it appears that when the LINE app opens an encrypted message and finds a link, it sends that link to a LINE server to generate the preview. We believe that this defeats the purpose of end-to-end encryption, since LINE servers know all about the links that are being sent through the app, and who's sharing which links to whom.
Even worse, some apps allow malicious actors to run arbitrary JavaScript code on remote servers via a well placed link.
We did find, however, at least two major apps that did this: Instagram and LinkedIn. We tested this by sending a link to a website on our server which contained JavaScript code that simply made a callback to our server. We were able to confirm that we had at least 20 seconds of execution time on these servers. It may not sound like much, and our code didn't really do anything bad, but hackers can be creative.
The full report is a great read if you're at all interested in what can happen when developers and back-end server architects don't think things through properly. Thankfully, some companies have already reacted to the findings of this report. Now we need the rest to follow suit.
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!

Oliver Haslam has written about Apple and the wider technology business for more than a decade with bylines on How-To Geek, PC Mag, iDownloadBlog, and many more. He has also been published in print for Macworld, including cover stories. At iMore, Oliver is involved in daily news coverage and, not being short of opinions, has been known to 'explain' those thoughts in more detail, too.
Having grown up using PCs and spending far too much money on graphics card and flashy RAM, Oliver switched to the Mac with a G5 iMac and hasn't looked back. Since then he's seen the growth of the smartphone world, backed by iPhone, and new product categories come and go. Current expertise includes iOS, macOS, streaming services, and pretty much anything that has a battery or plugs into a wall. Oliver also covers mobile gaming for iMore, with Apple Arcade a particular focus. He's been gaming since the Atari 2600 days and still struggles to comprehend the fact he can play console quality titles on his pocket computer.
