Bugs & Exploits
Latest about Bugs & Exploits
X opening random links every time you click on a post? It’s not just you — why isn’t everyone talking about this wild bug?
By Tammy Rogers published
If you click on an image in X's iPhone app, there's a chance you'll find yourself taken to a completely unrelated webpage — what is going on?

iPhone warning issued over exploit that fakes Airplane mode
By John-Anthony Disotto published
An exploit targeting users who turn on Airplane Mode has been found in iOS 16 according to new research.
Apple responds to claim of Mail app exploit in iOS 13
By Lory Gil published
Cybersecurity firm ZecOps claims to have found evidence of a zero-day exploit in the Mail app for iPhone and iPad. Apple says not to worry.

Users are experiencing yet another iOS autocorrect bug, and I.T stinks. Here's how to fix it!
By Tory Foulk last updated
Even though we've only just gotten over the A [?] bug, a new one has surfaced that turns "it" into "I.T."
Malware protection for older Macs
By Peter Cohen last updated
Some anti-malware software only supports newer versions of OS X. If you're running an older Mac, use this instead.

How to update your iPhone to fix Error 53
By Rene Ritchie last updated
Apple has released an iOS update to fix Error 53. Here's how to install it.

Multi-Touch Repair Program for iPhone 6 Plus
By Luke Filipowicz last updated
If the screen on your iPhone 6 Plus is malfunctioning, you may benefit from Apple's newest repair program.

Apple comments on Sidestepper, that supposed iOS MDM hijack security vulnerability...
By Rene Ritchie last updated
SideStepper isn't a new iOS vulnerability, it's an old phishing scam with new marketing.
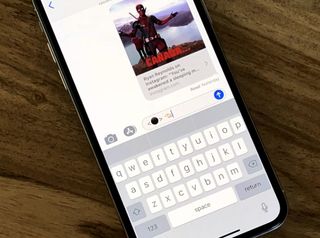
How to fix the 'Black Dot' Unicode bug on iPhone or iPad
By Rene Ritchie published
'Black Dot' — so-called because it's hidden inside '<⚫> 👈🏻' — is the latest Unicode-crashing text string being sent around iMessage.
Free Push Notifications with Push Doctor on your Hackivated iPhone
By IM Staff last updated

iPhone 5, iPod touch 5 touchscreens responding oddly to multiple, rapid diagonal swipes
By Rene Ritchie last updated
How to troubleshoot common jailbreak issues on iPhone, iPad, and iPod touch
By Allyson Kazmucha last updated

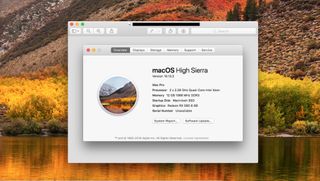
macOS High Sierra 'root' security bug: Here's how to fix it now!
By Rene Ritchie last updated
How to fix a missing serial number on macOS
By Anthony Casella last updated
Unable to access certain iCloud services? Missing a serial number? This fix may help!
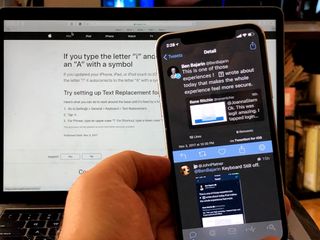
How to fix the annoying ! [?] text bug on iPhone and iPad
By Rene Ritchie last updated
Apple has pushed out iOS 11.1.1, a minor point release update that fixes the major annoyance of the letter i autocorrecting to I️.
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!