How to prevent unauthorized pairing with your iPhone or iPad using Apple Configurator
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!
You are now subscribed
Your newsletter sign-up was successful
When you connect your iPhone or iPad to iTunes on Mac or Windows, and choose to trust that computer, a pairing record is created that maintains that trust for future connections. There's a report going around that claims that if someone takes physical possession of your device and your computer, they can steal those pairing records and use them to retrieve your personal information and/or enable remote logging. If they don't have your computer, it's also claimed they can try and generate a pairing record by tricking you into connecting to a compromised accessory (juice jacking), like a dock, and/or by using mobile device management (MDM) tools intended for enterprise to get around safeguards like Apple's Trusted Device requestor. So, how can you protect yourself?
Important note: Security is at perpetual odds with convenience. This process will make your iPhone and iPad more secure but less convenient. It should only be used if a) even the potential for a privacy breach is untenable for you, and b) you really, absolutely can function without connecting your iPhone or iPad to other devices.
If someone has physical access to your devices, there are all sorts of things that can be done depending on their skill level, resources, and the value of your data to them. The information here is not meant to make anyone stressed or paranoid, simply to provide a specific option for a specific vulnerability in a vacuum.
Apple Configurator
Apple Configurator is a free tool from Apple meant to help schools, businesses, and institutions set up and manage large amounts of iPhones and iPads. With it, you can prevent your device from pairing with other computers or accessories, which prevents it generating pairing records, which prevents those records from being used to access your iPhone or iPad without your consent.
- Free - Download now app, available for free from Apple on the Mac App Store.
How to use the Apple Configurator to secure your iPhone or iPad against unauthorized pairing
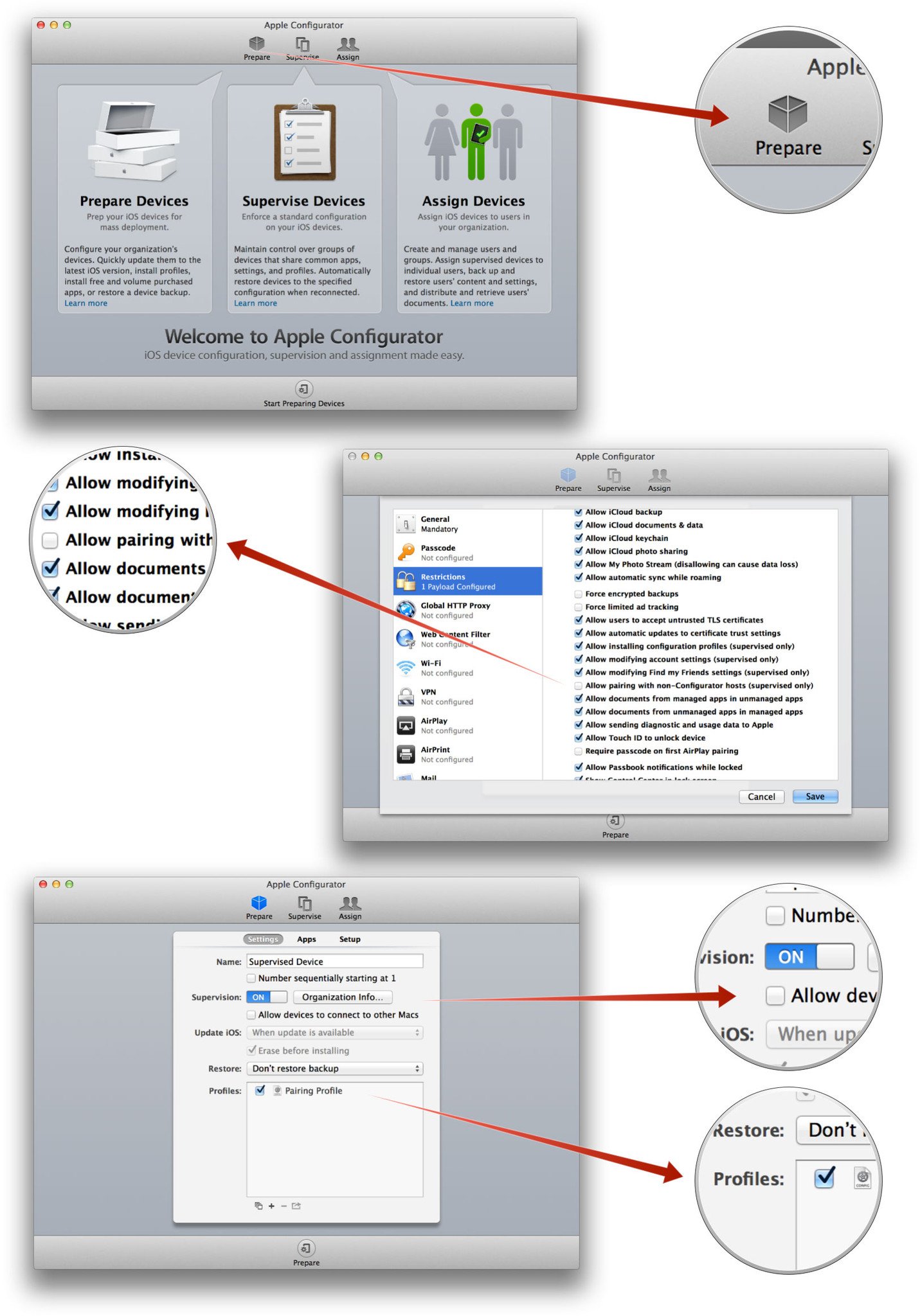
- Launch Apple Configurator
- Click on Prepare at the top
- Name the settings anything you like (e.g. Supervised Device)
- Click on Supervision to toggle it to on.
- Uncheck the box next to Allow devices to connect to other Macs
- Click on the + sign at the bottom
- Select Create New Profile from the popup
- Name the new profile anything you like (e.g. Pairing Profile)
- Click on Restrictions
- Click on Configure
- Scroll down to Allow pairing with non-Configurator hosts and uncheck its box.
- Click Save
- Check the box next to the new profile
- Click Prepare at the bottom
- Fill in the information you want displayed in the profile. (It doesn't have to be accurate, you can use 555-555-5555 for a phone number if you want to.)
- Click Apply
- Connect your iPhone, iPod touch, and/or iPad to apply the new settings
Additional security and privacy precautions
It should be noted that all the Apple Configurator does is prevent new pairing records from being generated, it does not delete existing records, nor does it protect against other types of hacking.
Apple doesn't currently provide a front end for deleting old or existing pairing records, either on OS X or iOS, which means you'll need to manually search for and try to remove them on your own (/var/db/lockdown or ~/Library/Lockdown on Mac or C:\Program Data\Apple\iTunes\Lockdown on Windows).
Someone else having physical access to your device or devices is in and of itself a massive security problem. However, there are some things you do to make it more difficult or time consuming for someone with your device to try and get to your data, including using a long, strong alphanumeric password instead of a passcode or Touch ID, and turning off Lock screen access for Control Center, Notification Center, Siri, Passbook, etc,. To prevent other types of remote access, you can enable two-step verification on your accounts and use unique passwords in conjunction with a password manager.
iMore offers spot-on advice and guidance from our team of experts, with decades of Apple device experience to lean on. Learn more with iMore!

Rene Ritchie is one of the most respected Apple analysts in the business, reaching a combined audience of over 40 million readers a month. His YouTube channel, Vector, has over 90 thousand subscribers and 14 million views and his podcasts, including Debug, have been downloaded over 20 million times. He also regularly co-hosts MacBreak Weekly for the TWiT network and co-hosted CES Live! and Talk Mobile. Based in Montreal, Rene is a former director of product marketing, web developer, and graphic designer. He's authored several books and appeared on numerous television and radio segments to discuss Apple and the technology industry. When not working, he likes to cook, grapple, and spend time with his friends and family.
